 Our customers rely on ReversingLabs Threat Analysis and Hunting Solution to provide them with an instant malware lab, delivering both static and dynamic analysis. Here, we break down the newest improvements to this necessary solution.
Our customers rely on ReversingLabs Threat Analysis and Hunting Solution to provide them with an instant malware lab, delivering both static and dynamic analysis. Here, we break down the newest improvements to this necessary solution.
ReversingLabs is proud to announce new features for ReversingLabs Threat Analysis and Hunting Solution (A1000 [PDF]). This solution offers customers an instant malware lab with static and dynamic analysis for all of your company’s files and binaries. The ReversingLabs Threat Analysis and Hunting Solution integrates with ReversingLabs file reputation services to provide in-depth rich context and threat classification. It supports visualization, APIs for automated workflows, global and local YARA rules matching, and integration with third-party sandbox tools.
Analysis outcomes are mapped to the industry standard MITRE ATT&CK framework for ease of use and correlation with other security solutions. This context allows analysts to effectively defend against both global and targeted attacks, accelerating investigations and response activities.
Our goal is for the ReversingLabs Threat Analysis and Hunting Solution to provide value in a number of ways for our customers. Reducing cyber risks while ensuring data and file privacy brings value to the businesses we work with. Additionally, our customers are able to reduce operational workload and tool costs. Practitioners benefit by using our solution's advanced technology to reduce MTTD and to prioritize malicious files for triage.
New and improved technology that drives security operations forward
In the most recent version of ReversingLabs Threat Analysis and Hunting Solution, several updates have been made to improve the overall quality and efficiency of our platform. No change is too small, such as redefining classification, creating clearer labels and interfaces, as well as sending necessary data to be included in dynamic analysis.
Bigger changes to our solution, such as the improvement of search workflows, user roles and permissions, sources section, and new download options will also bring benefits to our customers. Below, we break down these major solution updates for you.
Search workflow enhancements
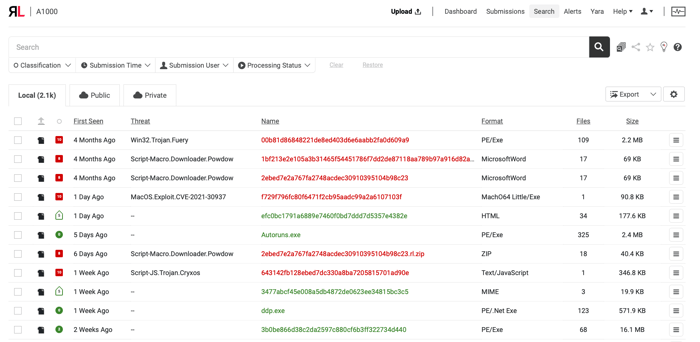
Having an accessible and smart interface on-top of ReversingLabs cutting-edge technology is an important part of our ReversingLabs Threat Analysis and Hunting Solution. This is why we have relied on customer feedback and internal testing to improve the Search Workflow for our customers.
With the newest version of the ReversingLabs Threat Analysis and Hunting Solution (A1000), users can more efficiently search for samples and interesting data within the ReversingLabs data corpus. Easily accessible dropdown filters have been added to the tool, as well as newly introduced local-only keywords. This improved user interface also prioritizes an enhanced Search feature as the central page for any investigation.
Having better search tools improves the effectiveness of an organization’s operations and practitioners. Our hope is that this new update to our solution does just that.
Enhanced user roles and permissions
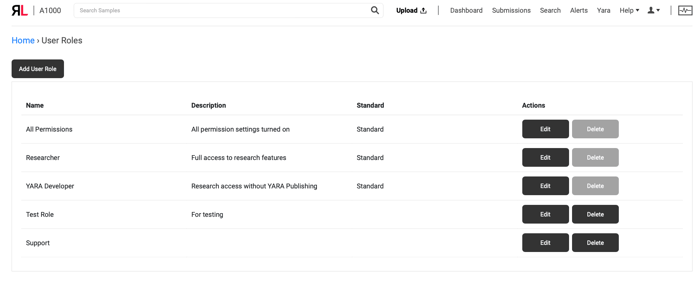
Users of ReversingLabs solutions need to be empowered to contribute to their organization by having the right access to tools, without excessive permissions. Because our customers have asked for more flexibility in assigning user permissions, this new enhancement provides administrators with more granularity for user access.
Now, the ReversingLabsThreat Analysis and Hunting Solution offers customizable user roles. We have also expanded permissions in the Submissions, YARA and YARA publish sections. More options for assigning user access reduces excess permission risk, plus it makes teams more productive with proper tool access.
An enriched sources section
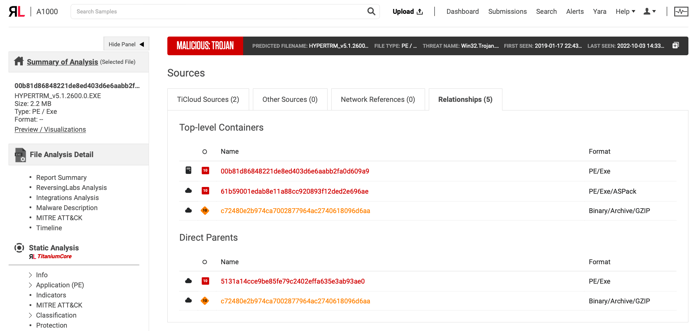
ReversingLabs strives to give our customers a prime view into the data they need to make critical cybersecurity decisions for their organizations. This is why the newest update to the ReversingLabs Threat Analysis and Hunting Solution platform includes a more comprehensive and helpful Sources Section for our customers.
Within the new version of this section, additional tabs have been added for Relationships and Network References. The Network References tab of this section assigns both classification and threat counts to URLs found on sample, while the Relationships tab shows which top-level containers the sample is connected to, as well as if the sample has any “direct parent” files.
This easy to access, tabular view in the Sources Section will greatly benefit practitioners, easing their use of the platform, as well as receiving additional metadata for file triage.
A downloadable report for the cloud sandbox
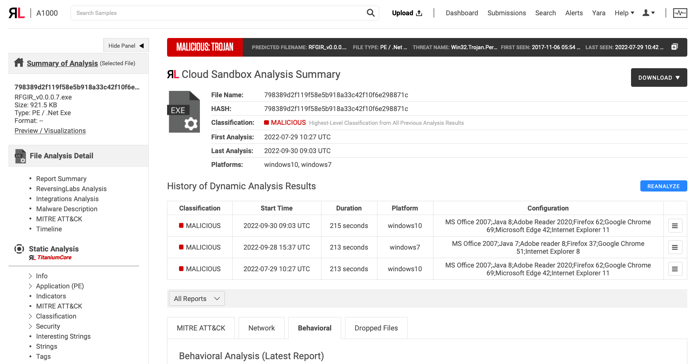
ReversingLabs wants its customers to be able to share the results of our solutions with other members of their organization and external partners who do not have direct access to the tool. Sharing valuable data provided by our ReversingLabs Threat Analysis and Hunting Solution between an organization’s teams and external partners will make our customers more successful.
This is why we have added a new feature to the Cloud Sandbox tool that allows users to download reports showing dynamic file analysis results, exported in either a PDF or HTML format. This will allow our customers to then share these reports with internal and external parties, as well as any other entity that helps their organization thrive.
Additionally, sharing threat analysis data to both internal and external sources will enhance a greater operational response to the most pressing threats.
Going above and beyond customers’ expectations
It’s clear to us at ReversingLabs that there is no true limit to improving solutions for our customers. This is exactly what we will continue to do with our ReversingLabs Threat Analysis and Hunting Solution, so that organizations can continue to have robust programs that can help mitigate today’s most serious malware threats.
Updates made to the most recent version of the ReversingLabs Threat Analysis and Hunting (A1000) platform, such as search workflows, user roles and permissions, an improved sources section, and a new downloadable report option, will benefit our customers and the mission of ReversingLabs. It’s also important to note that these major updates are just some of the key features that have been made to our Threat Analysis and Hunting solution.
Keep learning
- Get up to speed on Security Operations news and trends in our blog
- Explore how A1000 provides advanced hunting and investigations through high-speed automated static analysis and file reputation integration
About ReversingLabs
Over 10 years ago, ReversingLabs invented binary threat analysis to become the leading provider of file threat intelligence. ReversingLabs offers actionable context so IT and SOC teams can prioritize threats and optimize existing security tools. ReversingLabs solutions enable high-speed file classification via one of the largest malware and goodware sample repositories and expedite malware analysis with automated static and dynamic analysis. The most advanced security vendors use ReversingLabs solutions to enrich their file intelligence and provide better protection to their customers.
Get up to speed on key trends and learn expert insights with The State of Software Supply Chain Security 2024. Plus: Explore RL Spectra Assure for software supply chain security.






