The team at ReversingLabs has been hard at work and is proud to release the latest version of our A1000 Malware Analysis Workbench, version 6.0.
This milestone release delivers functionality that provides more detailed, explainable, and actionable analysis information than ever before while also making the interface more usable, informative, and intuitive for our users.
New Functionality and Classification
Several functionality updates have been made, including improving the global search capabilities and updating the YARA engine, but we want to call out two specifically.
The TitaniumCore engine now treats email as a native identification type. We’ve improved support for the formats that exist in different email systems. For example, Microsoft Outlook emails are now identified as “Email/None/OutlookMSG” and are supported by using a sample type keyword in the Advanced Search. Identifying an email more clearly allows analysts to classify and examine all samples that have been processed with TitaniumCore 4.0 more easily.
This may seem like a minor feature to call out, but the ability to generate a predicted file name during analysis is particularly helpful for distinguishing files that are only identified by their hash value. When you’re dealing with the thousands of files the A1000 can process every day, having a more familiar and searchable filename reduces the possibility of an error that may lead to a breach.
Automated Dynamic Analysis / Automation - ReversingLabs TitaniumCloud Sandbox
The A1000 has always been able to integrate with sandboxes for more detailed inspection. While users love the flexibility to send files to their existing tools, we’ve heard loud and clear that having the full analysis reporting in a single interface is just as valuable. This is why we’ve introduced a cloud-based dynamic analysis capability to the A1000. Adding dynamic analysis, or sandboxing, gives users a more efficient way to examine files that are particularly interesting and search the data in Titanium Cloud without having to jump between consoles. Because the capability is turned on by default, A1000 files are automatically enriched with existing dynamic analysis metadata. The great news is this service is based on the same dynamic analysis APIs available in TitaniumCloud, giving a consistent experience no matter how you use them.
Having a cloud-based sandbox built into the A1000 also means there are no additional resources needed to set up, configure, or maintain. Plus, if the sandbox has already processed the file, there is an option to skip analysis and reuse the existing metadata from the dynamic results. If you choose to re-analyze the file, all the previous analysis results will be stored and available for inspection. You can also create a merged report on all analyses to see if there are changes over time.
Focus on Usability
Providing human-readable explanations for why an indicator appears within the threat analysis report has always been important to our customers. The explainability gives senior analysts a quick way to prioritize indicators and a clear explanation for non-technical teammates. Since we make indicators human-readable, they simplify the code analysis process by converting complex code patterns into descriptions of their behavior. Version 6.0 has made some significant advancements with indicator transparency which makes it possible to describe the file behavior through descriptions like "Downloads a file" or "Encrypts or encodes data in memory using Windows API” so even the most junior member of the team can understand how malware works.
Keeping with the usability and education theme, we’ve improved our interactive storyteller feature that enables novice A1000 users to pivot through ReversingLabs extensive local and cloud data simply by clicking the description links, softening the advanced search syntax learning curve.
We’ve also added what we’re calling threat intelligence cards to provide an informative, educational overview and analytics on malware types and families in an easily accessible format on the Advanced Search page. Having a simple graphical report has been something customers have been asking to make it easier for non-technical teams to understand what’s happening during an investigation and after-action reports.

Increased MITRE ATT&CK Visibility
We all know the MITRE ATT&CK framework as an industry-wide standard for describing threats and actor behaviors through various tactics, techniques, and procedures (TTP). Presented as a matrix, it translates the attacker's actions into actionable concepts. These are neatly organized into matrices that consist of tactics that are in turn carried out by one or more attack techniques and sub-techniques.
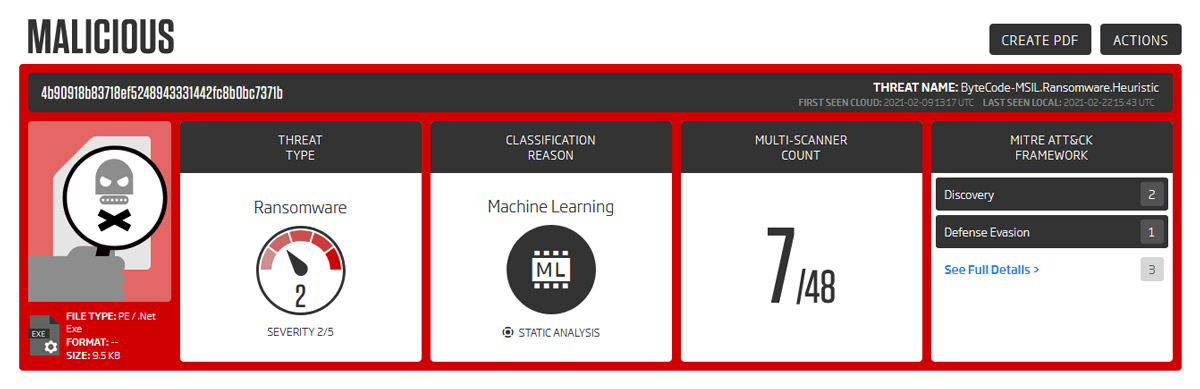
In the A1000, the page header for our MITRE ATT&CK mappings has been completely redesigned, making it easier to read sample classification information at a glance. The header now gives better prominence to the MITRE ATT&CK data, making it easier to access. The top 3 techniques by count are listed on the header, and a full, expandable list with ATT&CK data is now accessible directly on the summary page for faster viewing.
Expanding Out Of The Box Integration
Finally, no security product should stand alone, so we’ve been busy building new integrations and improving existing connectors to make it easier to use the vast amount of intelligence available to customers in both the A1000 and the Titanium Platform overall. Two notable changes in the A1000 include:
1) having options to delete the source files after analysis when using S3 and network file shares, limiting the number of locations you need to track for sensitive data or malware.
2) providing users access to historical information on all dynamic analyses with detected indicators of compromise being available to them through search and sections on the sample summary page.
This is just a taste of the improvements we’ve made in version 6.0, and you can find the full list of features and updates in the release notes. Over the next months, we’ll be releasing more integrations, and adding even more functionality to the Titanium Platform overall, so we’re not done. As I said, we’ve made many of these improvements based on your feedback, so keep it coming. Of course, if you want to learn more about what we’re doing, we’d be happy to set up a meeting.
- A1000 Malware Analysis Workbench Datasheet
- Dynamic Analysis API Datasheet
- To request a demo of these new capabilities, click here.
Get up to speed on key trends and learn expert insights with The State of Software Supply Chain Security 2024. Plus: Explore RL Spectra Assure for software supply chain security.







