Email-based attacks are a nightmare personified for every defender out there. The average organization receives thousands upon thousands of email messages carrying attachments and links every day. Each of those emails has the potential of being malicious, and any could slip by the existing array of defenses. And all those that do slip have but one purpose: to trick a single person into clicking a link that carries out a nefarious task.
Sometimes, all it takes is one person and one click. Once the attackers get it, they can redirect the link target to a credentials phishing page or a malicious file download.
It's very easy for a tech-savvy person to scoff and claim they would never be tricked in such a way. However, the number of these types of attacks is increasing, and they are always evolving. Each iteration is getting progressively harder to catch by simply glancing over the link. “Think before you click” might well be a thing of the past for some of the more sophisticated attacks out there.
To understand why, let's explore what some of those attacks looked like, and what they’ve evolved into.
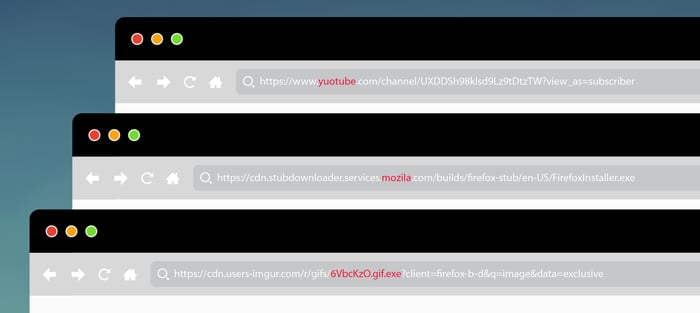
Link typosquat: Variant A
https://www.yuotube.com/channel/UXDDSh98klsd9Lz9tDtzTW?view_as=subscriber
URL analysis tags: [ #uri-domain-typosquat ]
Typosquatting is probably the oldest trick in the book when it comes to deceiving the user into thinking they are visiting a trusted website. It's a simple letter rearrangement attack that relies on the lack of user attention. Unsuspecting users can be tricked into visiting a rogue website and potentially expose their credentials through a convincing phishing page
Link typosquat: Variant B
https://cdn.stubdownloader.services.moziIa.com/builds/firefox-stub/en-US/FirefoxInstaller.exe
URL analysis tags: [ #uri-domain-typosquat, #uri-interesting-file ]
Some typosquatting attacks are harder to detect than others. A missing letter can be just as hard to spot as letter rearrangement. In this case, the deceptive link doesn't lead to a phishing page. Instead, it directly links to a malicious payload that will infect the user if downloaded. Given it looks like a browser installation link, the likelihood of it being executed increases drastically.
Deceptive file extension
https://cdn.users-imgur.com/r/gifs/6VbcKzO.gif.exe?client=firefox-b-d&q=image&data=exclusive
URL analysis tags: [ #uri-domain-spoofed, #uri-deceptive-file ]
Multiple file extensions are extremely hard for users to decipher. Most of the time, users skip to the first thing they recognize and act on it. Dual extensions, combined with long file names, play on the lack of expertise and hope to trick users into downloading and executing malicious content. Deceptive file extensions are typically coupled with misleading file icons, increasing the odds of a successful attack.
Trusted domain spoofing
https://www.google.com-amp-accounts.net/security/login.php
URL analysis tags: [ #uri-domain-spoofed ]
Attacks evolve as defenders improve their detection mechanisms. Trusted domains recently became even harder to recognize. This example is particularly hard to recognize, as it's using a trusted domain as a sub-domain for the domain highlighted in red. Since it's just a sub-domain, the attacker has the option of getting a valid certificate for it, resulting in a green lock icon next to the address in the browser window. This makes it next to impossible for the user to discern a rogue from a legitimate website.
Trusted link path spoofing
https://google.enterprise-login.com/signin/v2/identifier
URL analysis tags: [ #uri-path-spoofed ]
Habits are a funny thing. When users are conditioned to see a set of characters together every day, a sense of familiarity is formed. Just glancing over the link triggers this sense, and allows the deception to fly under the radar. Known login paths, like the one above, are perfect for such phishing attacks. Seeing them on unexpected domains is always a cause for alarm.
Trusted domain homoglyphs
https://accounts.gọọgle.com/servicelogin
URL analysis tags: [ #uri-domain-homoglyph ]
Perhaps the most difficult attack to detect by inspecting the link itself, homoglyph attacks are the latest trick in the attacker’s playbook. They became popular fairly recently when IANA (Internet Assigned Numbers Authority) opened up the Web to Unicode domain name registration. That made it possible to set up typosquat attacks that vary from hard to genuinely impossible to spot. The example above uses non-English alphabet to mask the letter “O” behind something that looks a lot like an “O”. Since the Unicode alphabet is quite large, the potential for these kinds of attacks is almost unlimited. That makes it the attacker’s new favorite toy.
Deception is at the core of most email phishing attacks. It relies on an ever-increasing number of ways the user can be misled into visiting a deceptive link. Because some of those deceptive links are impossible to spot with a naked eye, ReversingLabs has expanded its Titanium Platform with the capability to detect them.
Every example listed above - and many more alongside them - can be detected with our new static URL analysis technology. This new analysis component is deployed seamlessly to analyze any link our static file decomposition finds within emails, documents, multimedia, archives and programs. It gives the defenders a fighting chance by inspecting millions of emails an organization would typically see every month.
By looking deep within every single email, it’s fully capable of detecting that one bad link in an email forward chain within an attached archive that was a password-protected document. No other technology goes to these lengths to make sure the users are protected.
The extent of this feature is greater than just detecting deceptive links. Paired with the rest of our platform, it offers a unique link aggregation point. This provides the defenders with insights and pivot points around every link shared with their organization, whether the links come from the email body, or from any of the message attachments.
Get up to speed on key trends and learn expert insights with The State of Software Supply Chain Security 2024. Plus: Explore RL Spectra Assure for software supply chain security.






