
Email-based attacks are the most prominent threat vector that organizations see today. Like any other form of communication, emails get exploited to become carriers for a wide variety of attacks. Securing email nowadays means worrying about malicious attachments, links leading to malware, links leading to phishing sites, and business email compromise attacks.
Due to their nature, those attacks are commonly perceived as threats external to the organization. However, when the organization is already compromised, internal emails can become a tool used by the attacker to move laterally through the organization. In some cases, they are the stealthiest choice, as some organizations only perform security checks against incoming emails.
The following analysis is a reconstruction of an attack on a manufacturing company with ties to aerospace and defense industries.
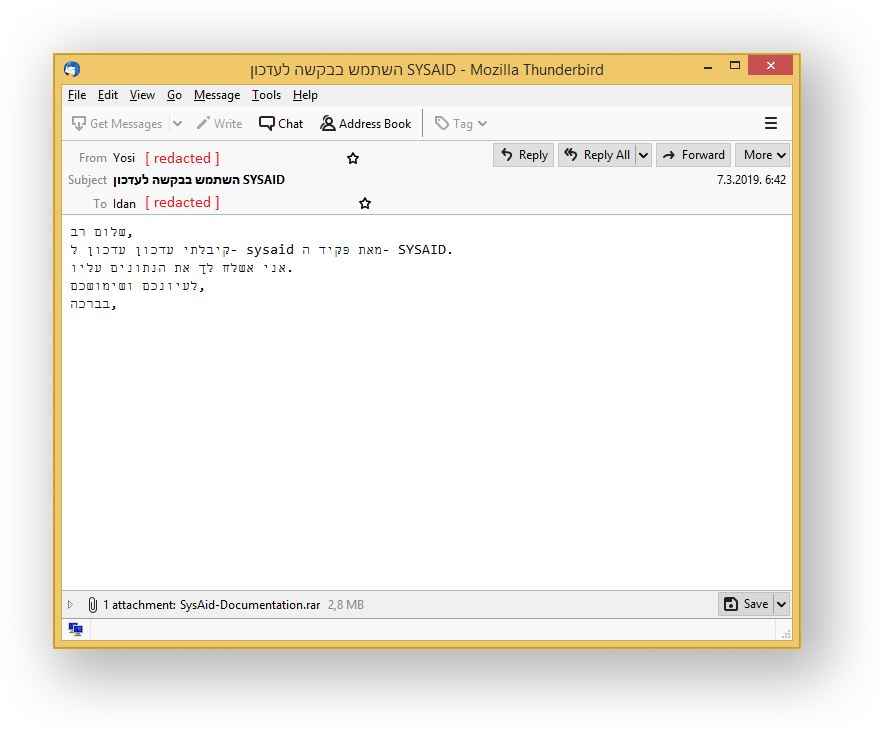
Yosi and Idan both work for a compromised manufacturing company. Yosi, a mechanical engineer, is sending an email to Idan. He is notifying his colleague about changes to their helpdesk software. The email contains a short message about the documentation that he’s attached.
When run through an automated language translation service, the message reads something like this.
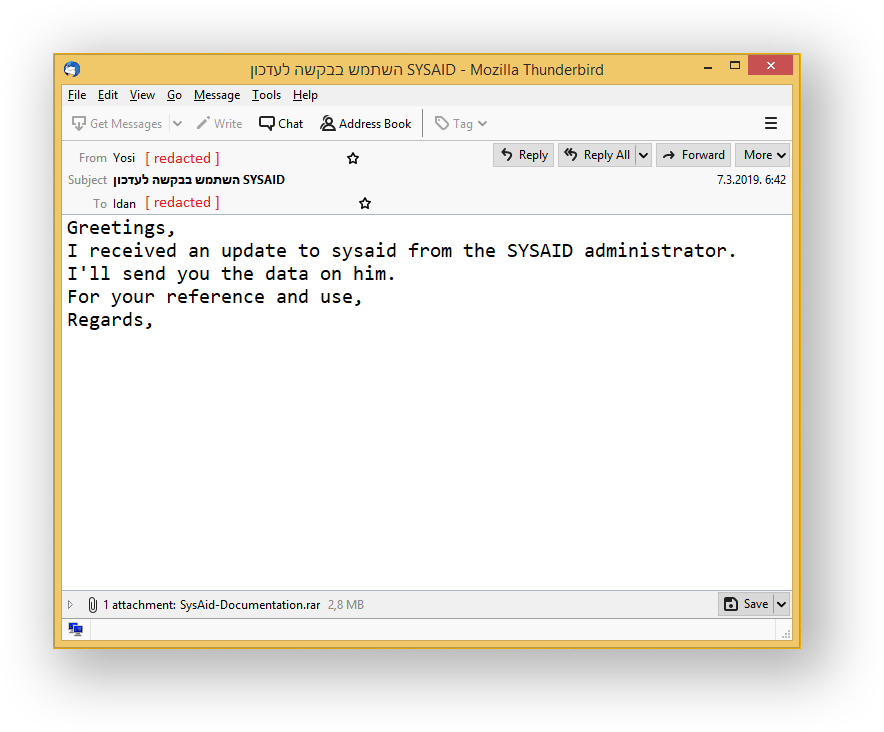
Sounds quite convincing. Since Idan trusts his coworker Yosi, he feels comfortable opening the attachment. There’s no reason for Idan to suspect that Yosi isn’t the one sending him the email. The email is sent from Yosi’s email address; it has the same reply-to address. Even if Idan put in the extra effort to inspect the email headers, all he would see is that the email was routed through the internal mail server.
However, that attachment is not a RAR archive despite its file extension. In reality, it is an ACE archive - a format that WinRAR knows how to open. Within WinRAR, the ACE format support is provided by a freeware library made by the WinACE authors.
That library has recently been found to be affected by a path traversal vulnerability - an issue that allows an attacker to place a file in an arbitrary folder on the system. This vulnerability can be used to place an executable file in just the right place for it to launch the next time the machine powers up. That is exactly what the attachment is trying to do.
ReversingLabs A1000 visualizes the email headers and allows analysts to browse email contents. Email attachments - when they are an archive - are extracted and displayed in a view similar to one of an archive manager. The image below shows the contents of the ACE archive Yosi sent to Idan.
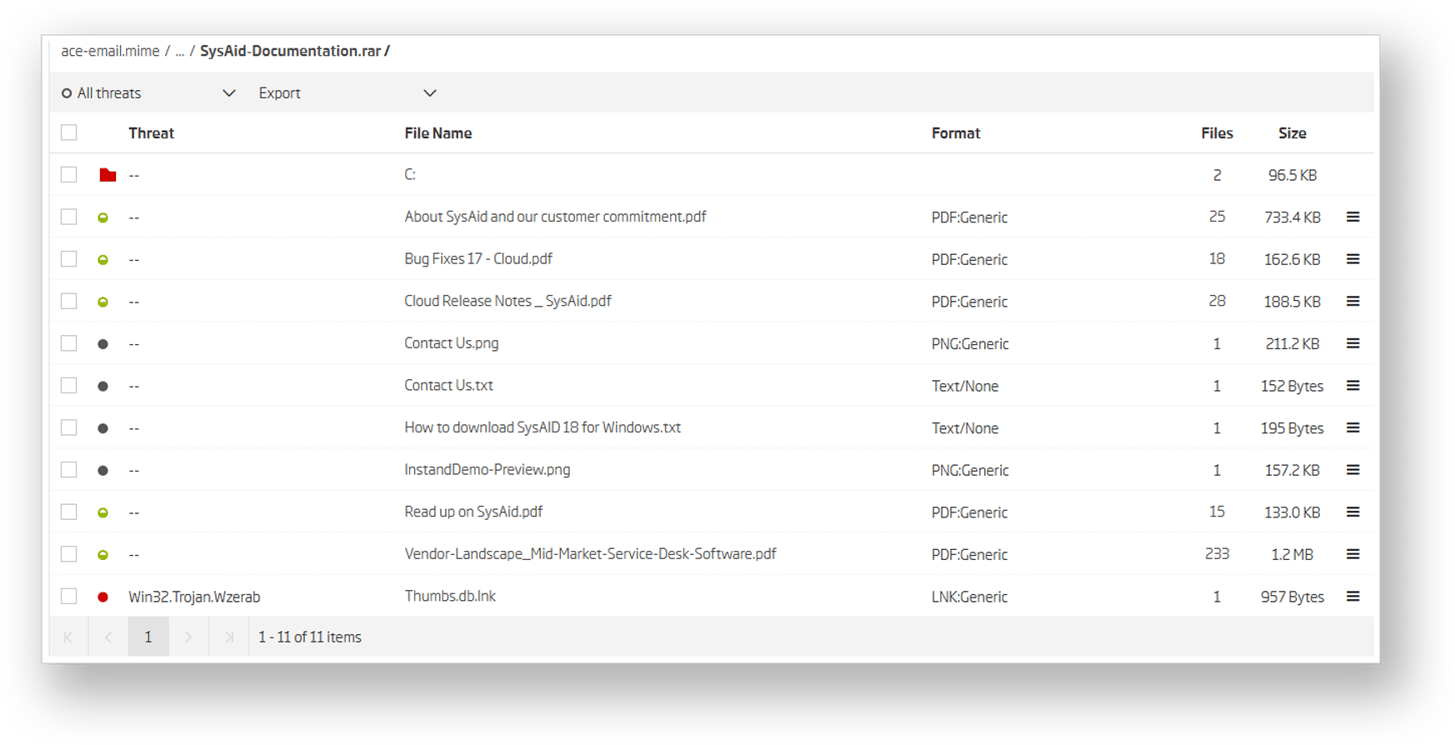
The documentation that Yosi promised to Idan is certainly there. There’s lots of it, and it is used to cover the fact that Yosi is not who he claims to be. The first folder in the list of files is an indication that the attached ACE archive is exploiting the path traversal vulnerability - assigned CVE-2018-20250.
Following the folder path all the way down, it is easy to see where the following executable file is going to be extracted to.
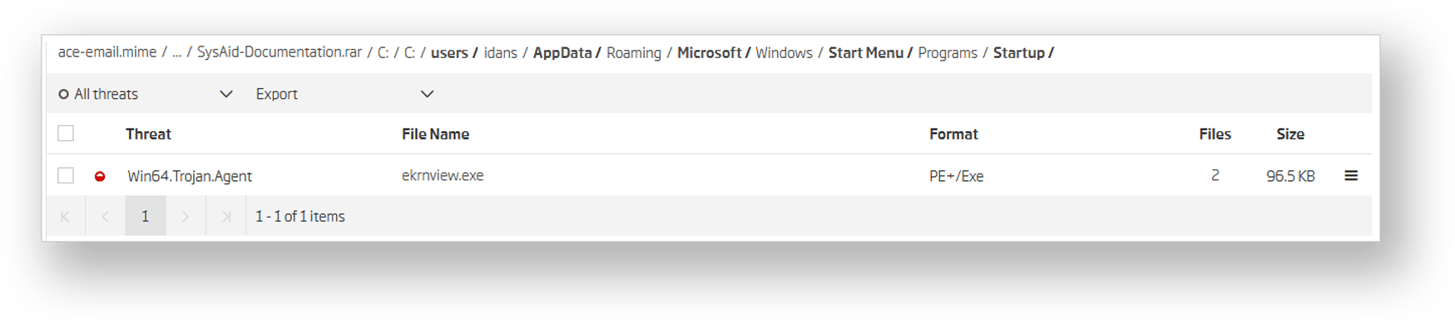
Not only is the executable installed to the startup location, but it is also clear that this attack is a highly personalized one. The path traversal only works because the absolute paths are hardcoded to point to the user-specific startup folder. That makes the attack viable only for the machine of the intended email recipient, Idan.
At this point, it is clear that the attacker has compromised the organization. That Yosi’s credentials are in the hands of the attacker. That the recon phase of the attack has been completed, and that the attacker is interested in moving laterally through the organization. It is more than likely that the next target, Idan, has access or information that the attacker is ultimately after.
The malicious executable the attacker expects to have successfully planted on Idan’s machine reveals more about the who and the why.
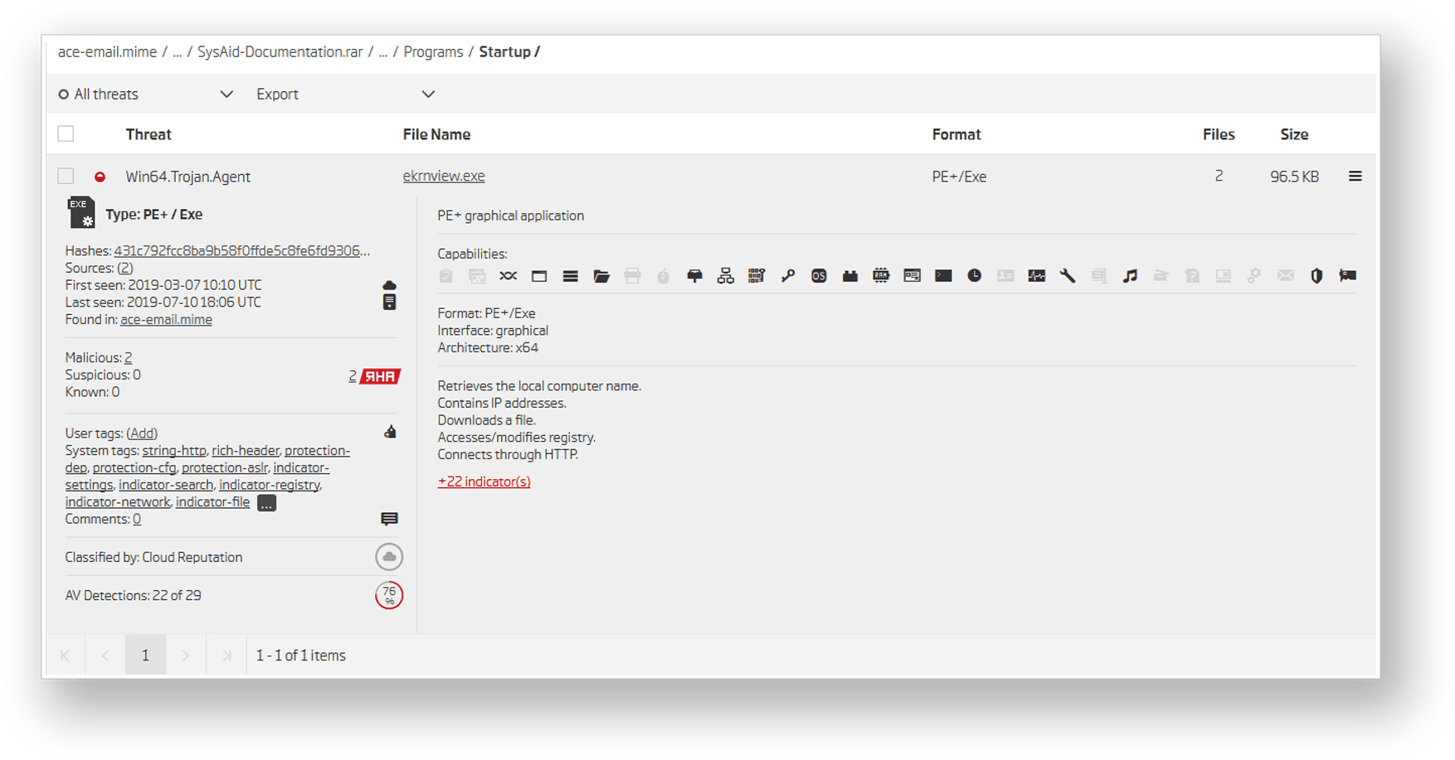
While "Agent" is not a particularly interesting or indicative threat name produced by our system, it is a starting point. It means that the threat itself isn’t particularly unique, and that it shares at least some of the commonality with previously discovered trojans. This is where functional code similarity can help. There is exactly one more file in the ReversingLabs cloud system similar to the one we’re looking at.
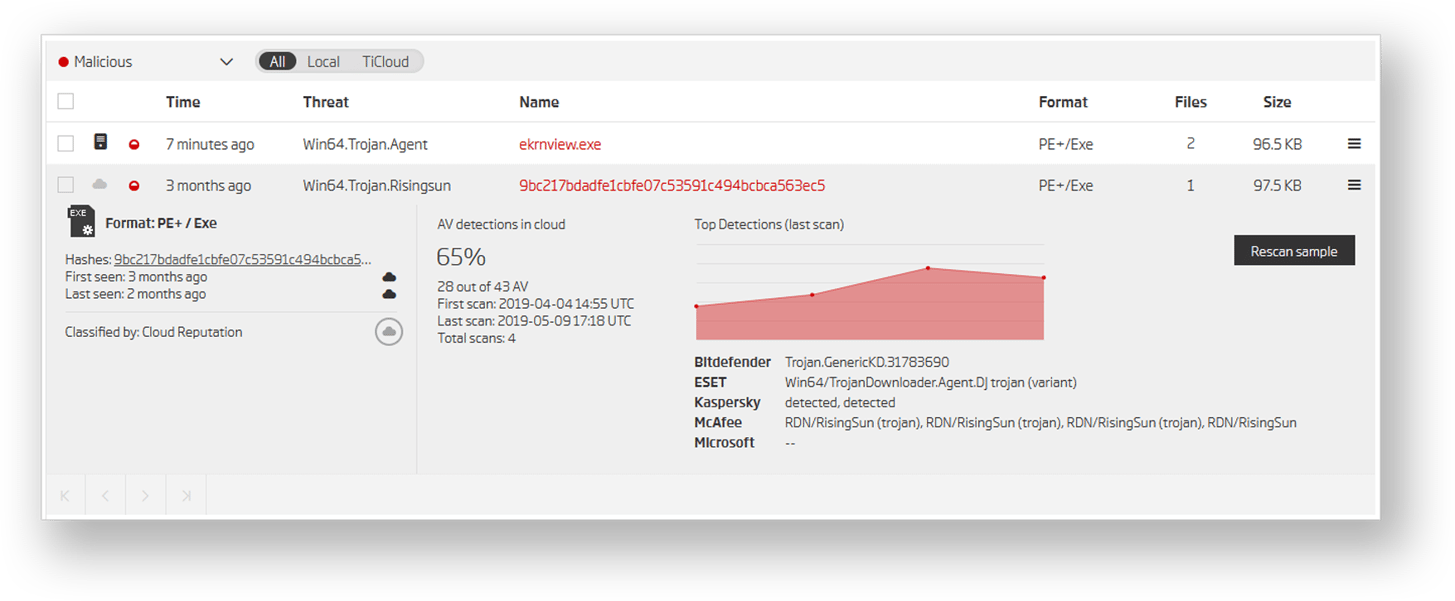
That file has been classified as RisingSun Trojan by McAfee. The report which McAfee’s Advanced Threat Research team published on the Operation Sharpshooter describes what we’ve seen so far perfectly - an advanced attacker targeting the defense sector.
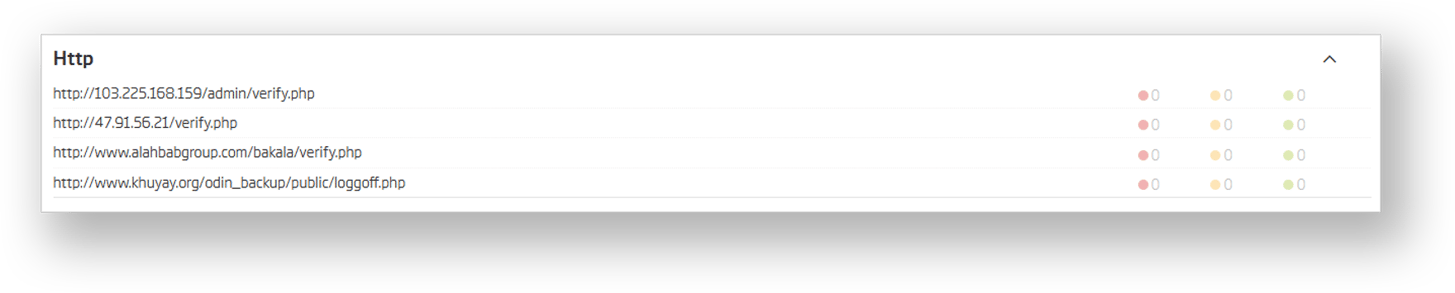
The suspicion that the attacks are connected is further supported by URLs extracted from the relevant executable. They seem to follow the same pattern as described in McAfee’s report.
A look at the executable hex dump also reveals a few striking similarities between the attacks.
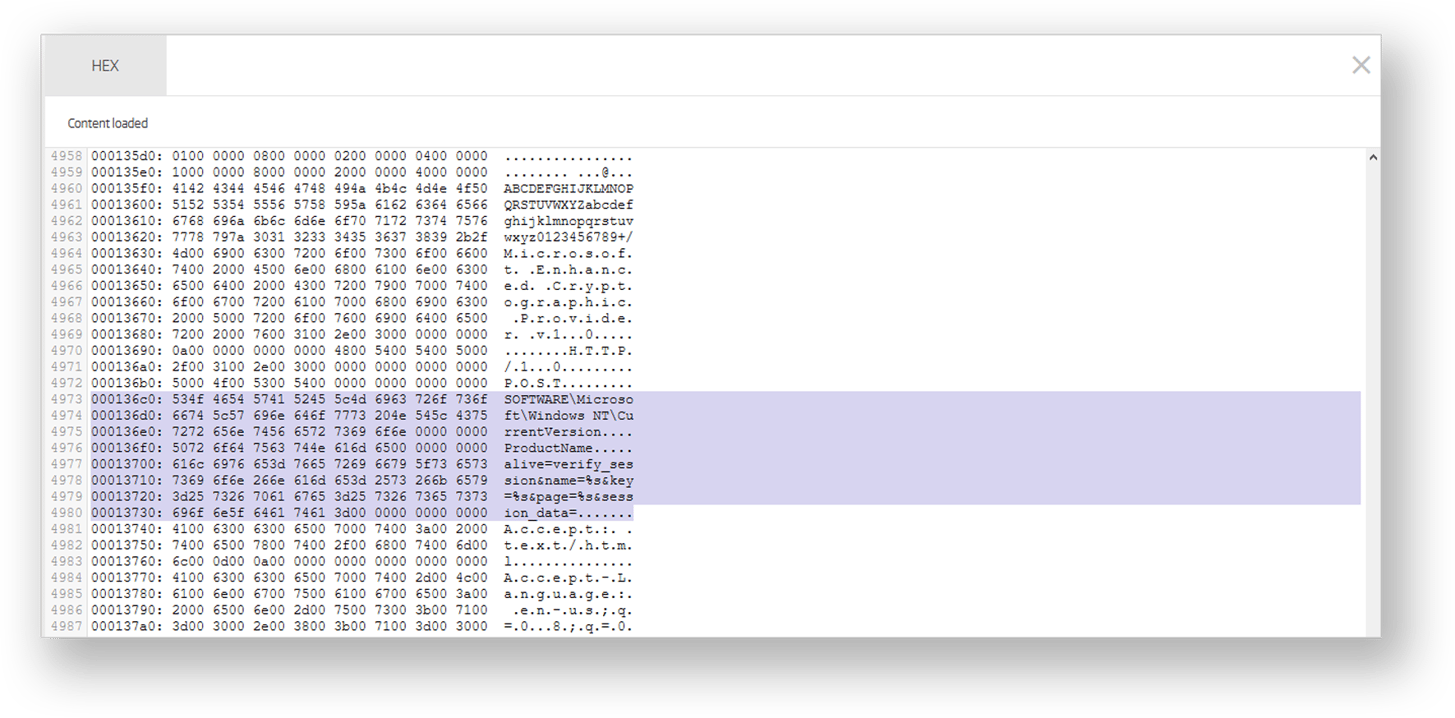
The email Yosi sent to Idan may very well be an indication of new activity for this APT actor. While the infection techniques seem to have evolved since McAfee published their report in December 2018, the methods of operation remained similar. The list of targets the actor is interested in has apparently been expanded to a new region as well - Israel.
Scouring the web for additional information based on what’s been discovered at this point reveals one more report published by the FireEye Threat Research team. They go into the analysis of this same email, so it is recommended to read their report as a follow-up to our discussion here.
Email is an important threat-carrying vector. Securing an organization's email infrastructure mandates checking all emails received by the organization, whether they are coming from the outside or from within. The ReversingLabs Titanium platform enables such deep inspection with its elastic file processing capabilities. With our platform, the possibility of checking every email message the organization sees becomes the norm. Deploying such a capability within an organization could make the difference between catching the lateral email movement and missing it altogether.
IOC:
MIME - 5b5d7d74db59c520b72be1e328563a1ee864e8931a0ae7487d753ee3e166de1c
URL:
http://www[.]alahbabgroup[.]com/bakala/verify.php
http://www[.]khuyay[.]org/odin_backup/public/loggoff.php
http://103[.]225[.]168[.]159/admin/verify.php
http://47[.]91[.]56[.]21/verify.php
Read our prior blog in the series on Ransomware in exotic email attachments.
Get up to speed on key trends and learn expert insights with The State of Software Supply Chain Security 2024. Plus: Explore RL Spectra Assure for software supply chain security.







