
We’ve seen some exciting customer results from our partnership with Tanium. This blog focuses on the results and lessons learned from a proof of concept (PoC) completed with one of these customers.
ReversingLabs and Tanium products have out-of-the-box integration to provide a powerful solution for rapidly identifying and remediating undetected malware on endpoints. The Tanium platform provides unprecedented visibility and access to endpoints in an organization’s network. Customers can use the platform to pose questions to determine the current state of all endpoints in real time. For example, a customer can use Tanium to query their endpoints and get hashes of all processes that have run, files in Download folders, or newly installed files. ReversingLabs File Intelligence enriches this collected hash data to identify undetected malware to both speed and prioritize responses.
Case Study
A midsized company with 20,000 endpoints had all the expected detection defenses including AV, sandbox, IPS, anomaly detection, and SIEM. In spite of this, malware still frequently infected their systems. To combat this situation, the company’s security team initially installed Tanium and was very impressed with the visibility it provided. However, the challenge with increased visibility is that it returns a large volume of file hashes that require investigation to expose potential threats.
To assess the hashes returned by Tanium, the security team used a cloud service that provided a count of the number of AV engine detections for each file. The team assumed that the higher the count of AV detections for a given file, the higher the likelihood that it was malware. Conversely, the lower the count, the greater the likelihood that it was a false positive. This approach turned out to be unreliable since new attacks are detected by only a few highly reliable scanners, if at all.
ReversingLabs understands this, and its analysis algorithm takes into account not only the rate of AV detection but also a number of other file attributes in formulating its assessments. These include functional similarity to other malware, high rates of entropy, bad certificates, and more. The screenshots below show files with low AV detection rates but high threat levels and severity scores from ReversingLabs analysis.
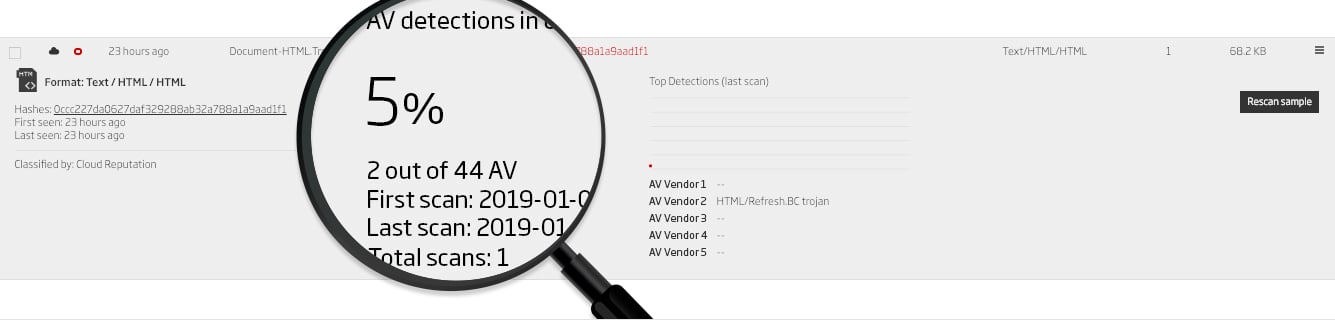
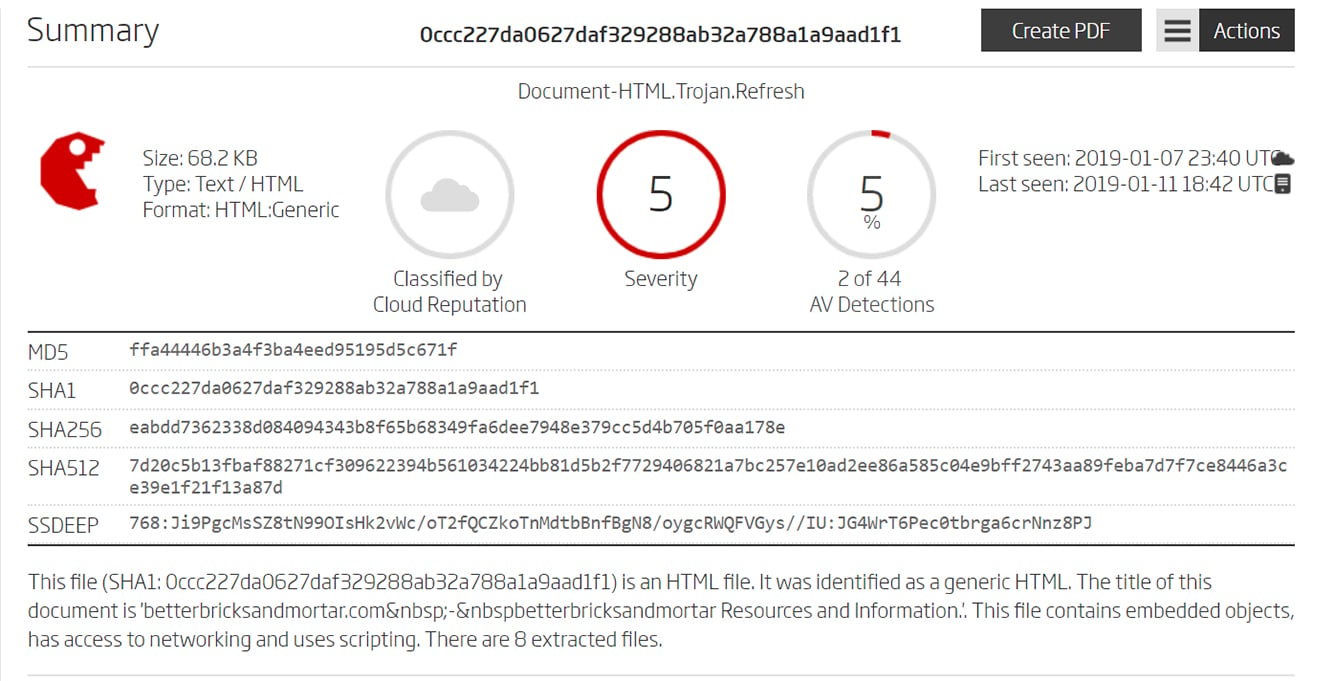
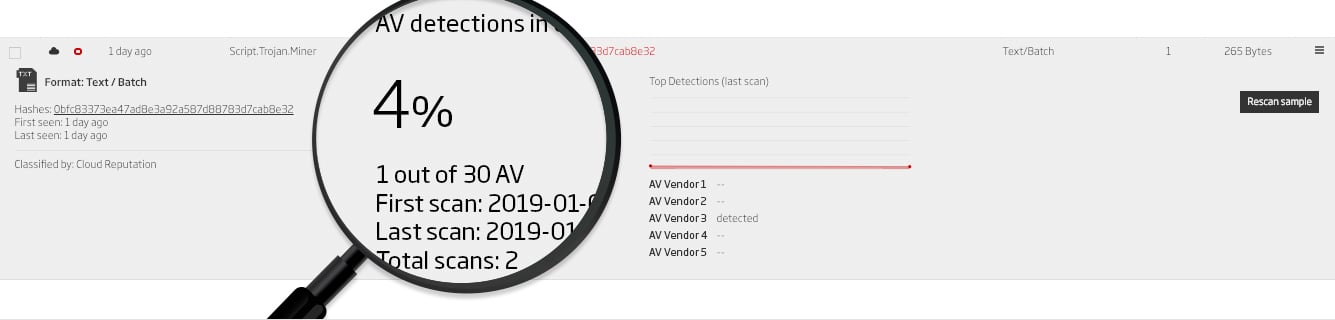
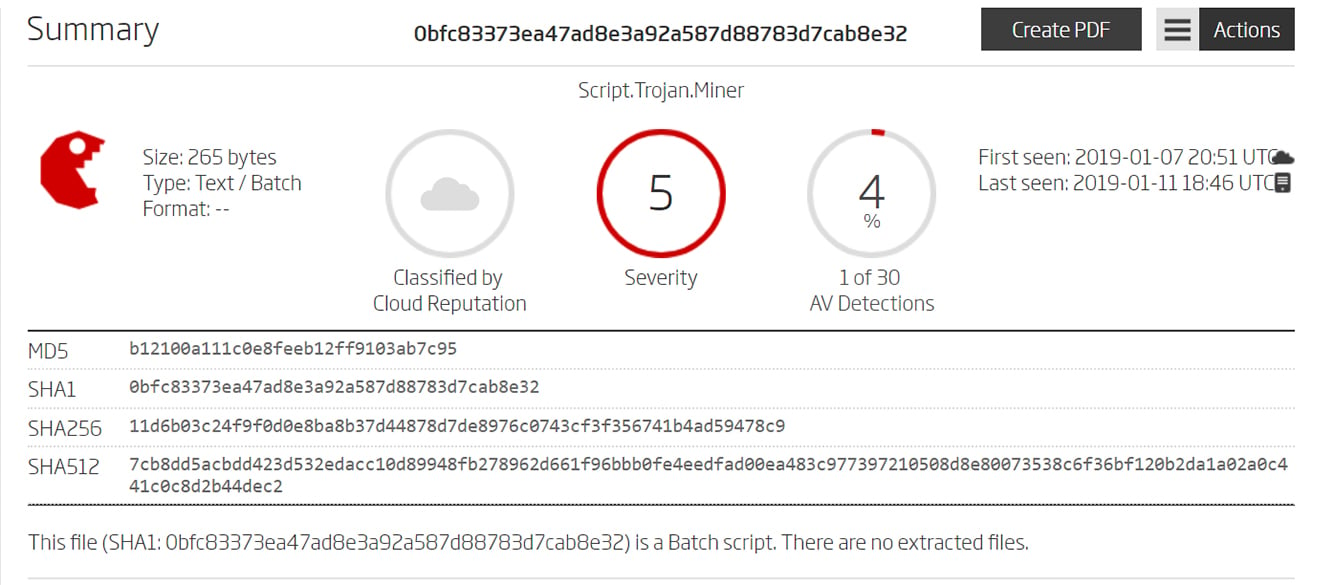
Examples of files with low AV detection rates, but high-risk scores based on ReversingLabs analysis
The company had another challenge. They did not have a large security team, and as Tanium returned hashes for analysis, it took security analysts several minutes to cut and paste them all into the AV scanner/reputation cloud service. Analysts knew they were getting bogged down by this manual process when their time should have been spent more productively on analyzing the results.
To kick off the customer engagement, ReversingLabs did a one-week PoC to test the advantages of ReversingLabs analysis capabilities and the automation created with the Tanium/ReversingLabs integration. Tanium was set up to query all endpoints hourly and retrieve file hashes from several different locations. These queries generated results of about two million files per day. All of those files were automatically analyzed by ReversingLabs TitaniumCloud File Intelligence Service with the results displayed directly in the Tanium console.
Using Tanium and ReversingLabs, the security team was able to identify almost 500 previously undetected malware samples on their endpoints (see graphs below showing the results of the PoC). Many of these malware samples had dwell times of more than a year.
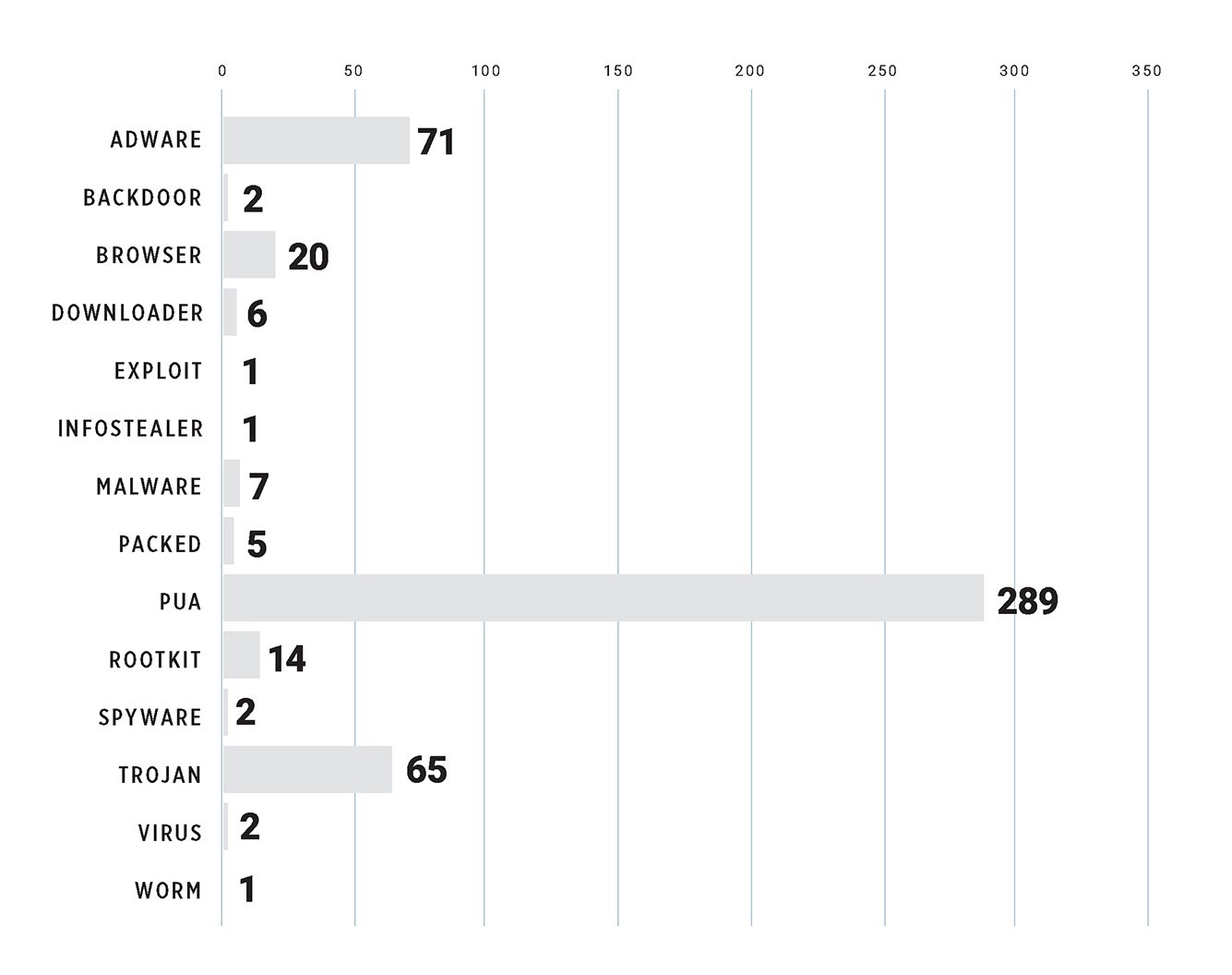 Undetected malware found on customer's endpoints by type
Undetected malware found on customer's endpoints by type
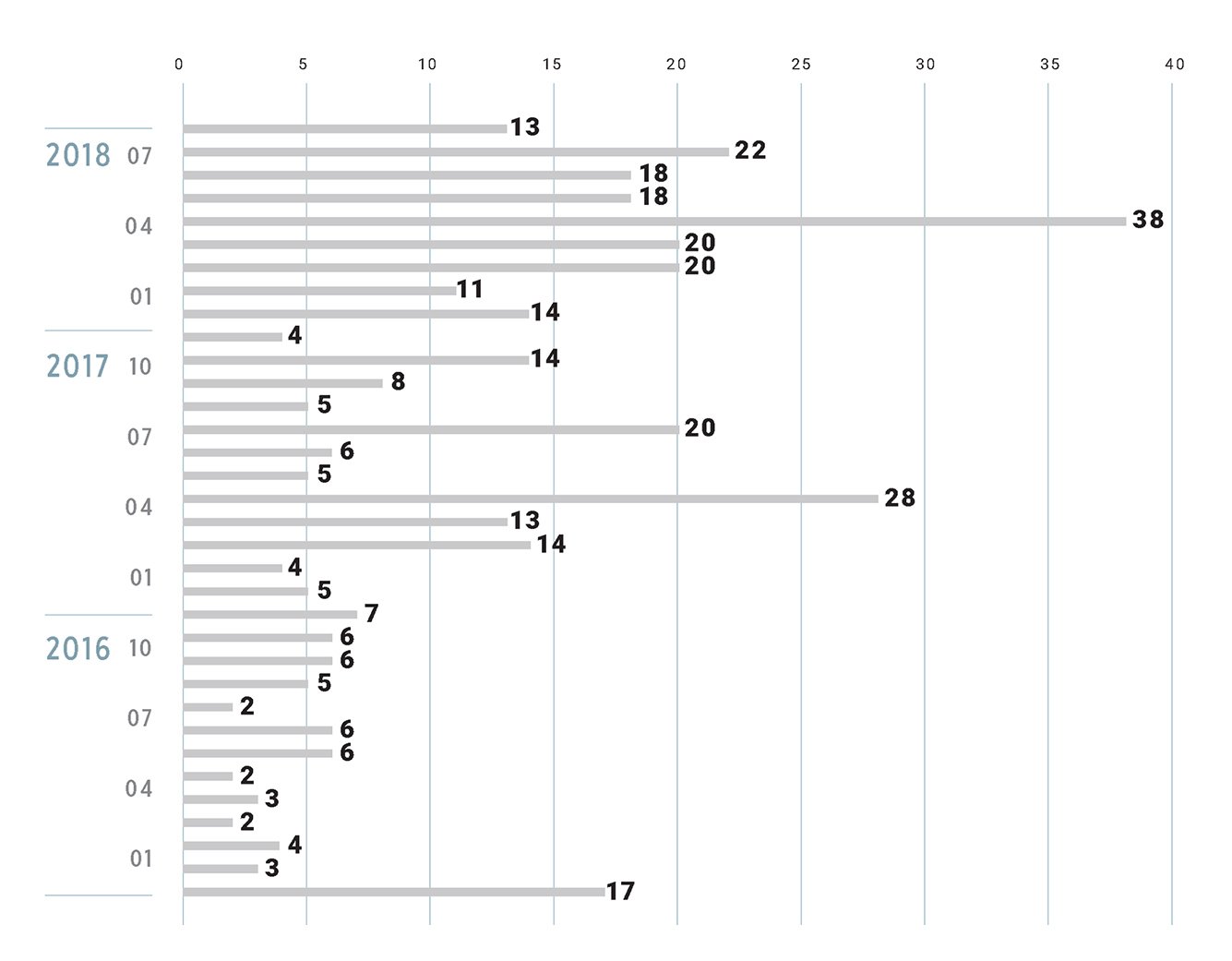 Number of malware samples on customer’s endpoints, first seen by ReversingLabs
Number of malware samples on customer’s endpoints, first seen by ReversingLabs
The PoC was a tremendous success. The company filled the visibility gap that existed around undetected malware, and the automation created by the ReversingLabs and Tanium integration enabled its relatively small security team to spend more time identifying, analyzing, and containing the malware that was attacking their endpoints. Several elements contributed to this success, including ReversingLabs:
- Ability to automatically enrich Tanium results with file intelligence to quickly identify a file’s threat level severity, name, and type,
- Delivery of the industry’s most up-to-date, comprehensive intelligence on malware and goodware, and
- Providing access to file intelligence without having to leave the Tanium UI, and the ability to use Tanium’s filtering capabilities to zoom in on the most critical malware.
The company continues to see excellent results from the joint deployment and has expanded its use of both solutions. This example, along with the successes seen by other joint Tanium/ReversingLabs customers lead Jesse Harris, Dir Technical Account Management at Tanium, to comment, “Every Tanium customer should take the time to see a demo of the integrated solution so they truly understand the power and speed ReversingLabs’ capabilities will add to their detection, analysis and containment operations.”
See a demo of the integrated Tanium/ReversingLabs Solution
An Integrated Solution
The integration of ReversingLabs File Intelligence service with the Tanium platform enables Tanium users to significantly reduce the time and effort required to filter and evaluate file hashes returned by endpoints. When the Tanium platform encounters a file hash, it requests, and stores file reputation information from ReversingLabs’ File Intelligence Service. The Tanium UI filters and displays the resulting file meta-data, including threat level, severity, name, and type. This provides critical decision-making information without the need to cut & paste hashes or leave the Tanium UI for another tool to identify files. This enables much faster and more efficient reviews of results, less tedious analysis, and more accurate malware identification. It also helps SOC analysts to quickly focus on the most dangerous files and understand the threat type (e.g., ransomware vs. adware) to inform the proper response.
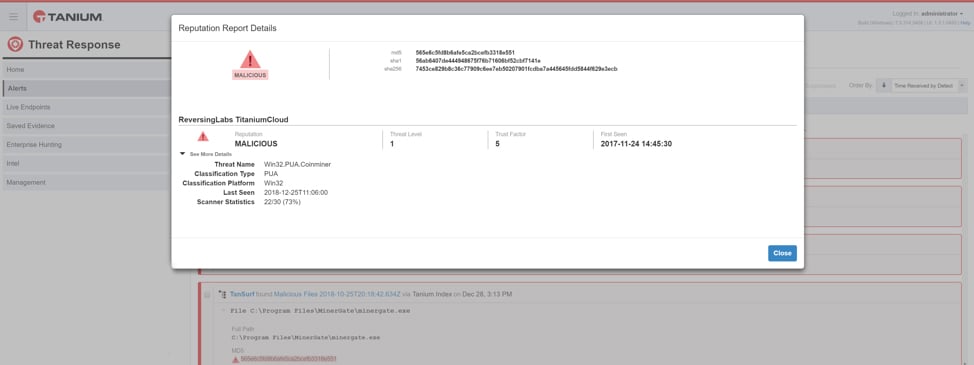
Actionable file intelligence from ReversingLabs displayed in Tanium UI to speed response
Existing solutions that return a thumbs up/down rating or the raw number of A/V detections, force security teams to implement simplistic, threshold-based approaches. Those approaches, such as setting an AV detection rate (e.g., 10 of 40 AV engines detect a file as malware) do not provide good indicators for advanced or unknown malware. That’s because only a few AV engines may initially detect this malware. ReversingLabs provides qualitative meta-data and context well beyond AV counts, such as threat level, trust factor, and classification type, enabling customers to make better, more informed response decisions.
TitaniumCloud File Intelligence
ReversingLabs’ TitaniumCloud Intelligence Services provide the industry’s most comprehensive and private threat intelligence solutions with current threat classification and rich context on over 8 billion goodware and malware files. ReversingLabs does not depend on crowd-sourced collection but instead curates the harvesting of files from software vendors and diverse malware sources. All files are processed using ReversingLabs Automated File Decomposition technology to provide multi-factor classification and context for each file. TitaniumCloud supports a robust set of REST API query and feed functions that deliver targeted file and malware intelligence for threat identification, analysis, intelligence development, and hunting.
Learn more about our Tanium Integration
Learn more about TitaniumCloud File Intelligence Service
Get up to speed on key trends and learn expert insights with The State of Software Supply Chain Security 2024. Plus: Explore RL Spectra Assure for software supply chain security.






