
Background:
On July 9th 2018 ESET published a blog indicating strains of Plead malware are misusing D-Link certificates.
Since then, D-Link has revoked those compromised certs.
https://securityadvisories.dlink.com/announcement/publication.aspx?name=SAP10089
Hashes mentioned in the blog are not available on VTI or public space. ESET has marked them as private. ReversingLabs Research obtained 2/4 hashes.
Topic interest trend:
Use case:
Demonstrate search capabilities in hunting for malicious samples that are using valid or revoked certificates.
cert chain: https://docs.microsoft.com/en-us/windows/desktop/SecCrypto/certificate-chains
RL Research
On July 3, 2018, D-Link, a well-known multinational networking equipment manufacturer headquartered in Taipei, notified customers that the company had revoked two of its code-signing certificates that were misused by unknown attackers to sign malicious code. The incident was first brought to D-Link’s attention by ESET researchers who detected that Plead malware samples were using those certificates to avoid detection by anti-virus (AV) vendors.
The technique of signing code with certificates from reputable companies is not new. In recent years this approach has been successfully used by Stuxnet (which used stolen digital certificates from Realtek and JMicron), Piriform Ccleaner, and others. Spotting certificate misuse in a timely manner is crucial for preventing further damage and protecting customer data.
Threat hunting scenarios for certificate misuse include using information such as certificate thumbprint, Issuer of the certificate, certificate authority, name of the organization to whom the certificate has been issued, or serial number of the file certificate.
Join ReversingLabs Research (RL Research) on a Threat Hunt for revoked D-Link certificates. Let’s begin.
Step 1 - Pivoting on revoked D-Link certificates:
https://securityadvisories.dlink.com/announcement/publication.aspx?name=SAP10089
cert-serial:[130303E4570C272909E265DDB859DEEF, 01a586a95b44609e9fae25f9277962d6]
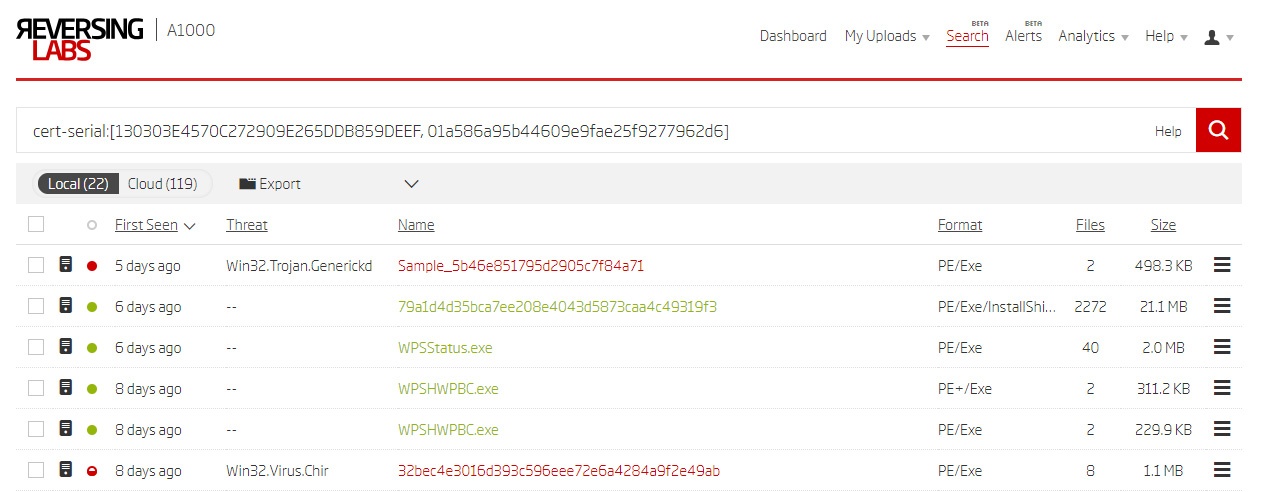
The above results show two malicious samples (highlighted in red). Both have a story to tell.
A.) Sample 1db4650a89bc7c810953160c6e41a36547e8cf0b:
The first sample is a file signed with a D-Link certificate (cert-serial:130303E4570C272909E265DDB859DEEF) and classified as malicious by multiple AV engines. This certificate was previously used for signing legitimate D-Link programs, so this malicious sample proves that the certificate was stolen.
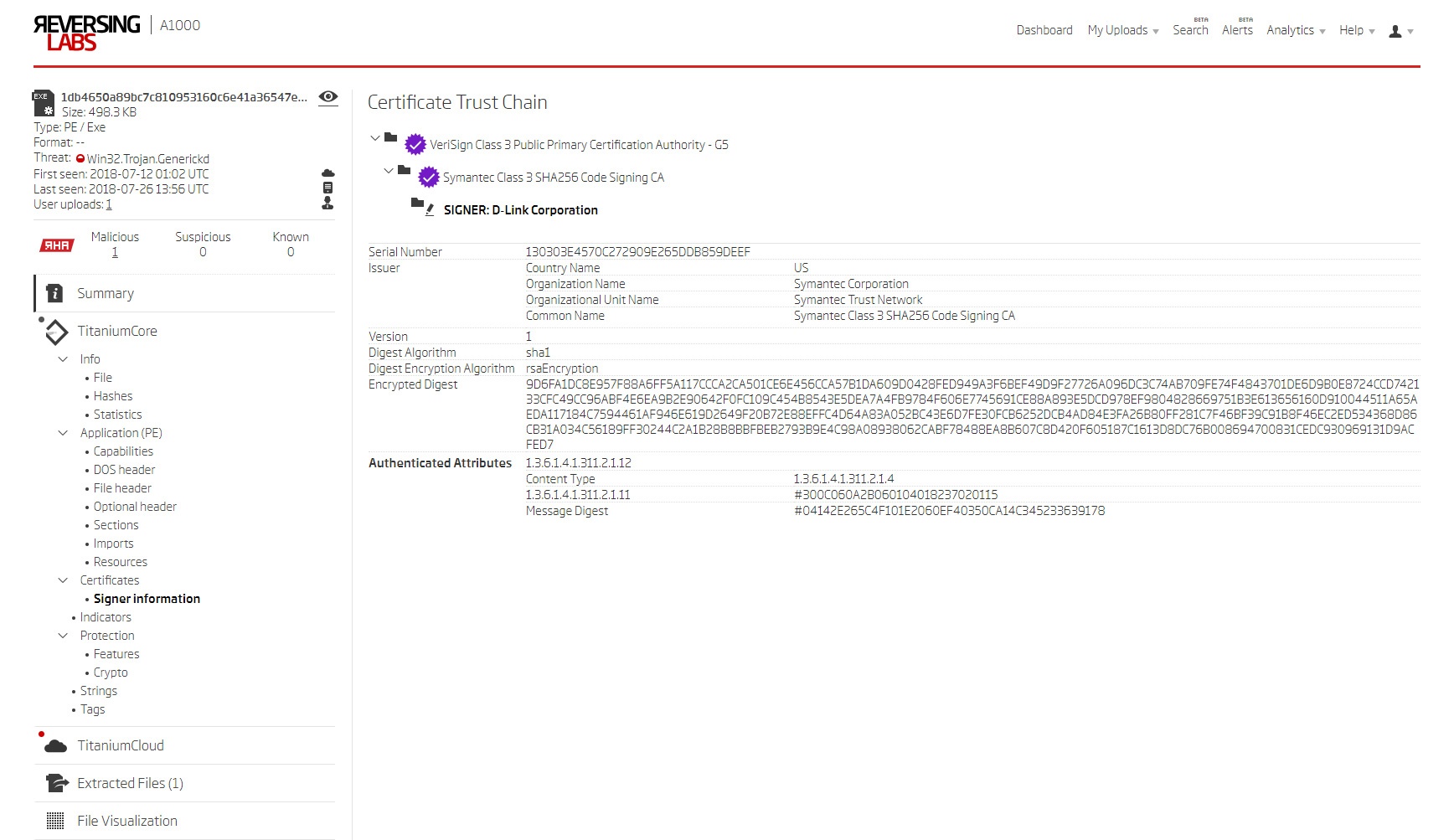
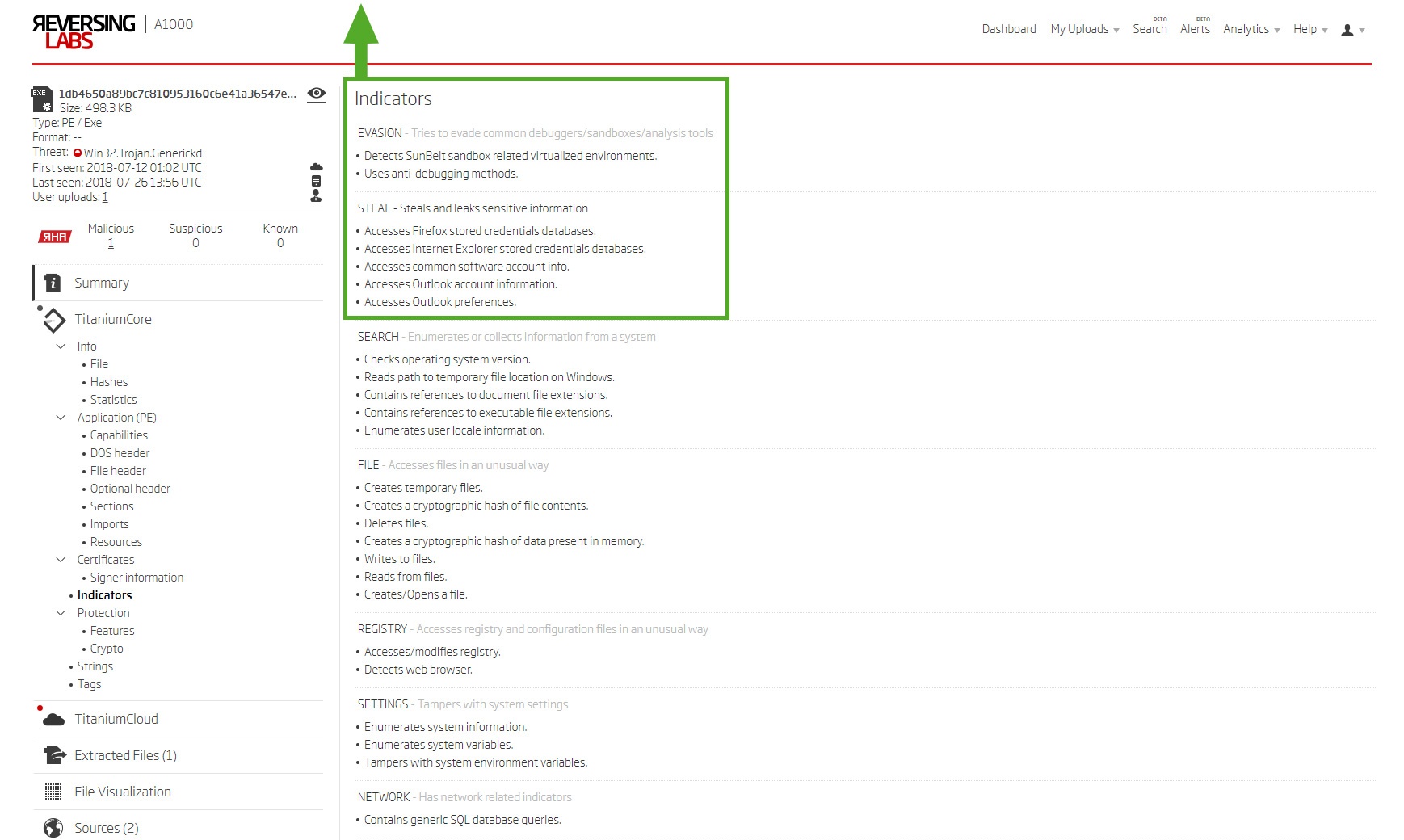
Utilizing the ReversingLabs A1000 Malware Analysis platform to speed up the process, we extracted indicators from the sample. All the indicators agree with AV engines exposing Trojan and credential-stealing capabilities. In this case, the malware is looking for browser and email client credentials.
- EVASION - Tries to elude common debuggers/sandboxes/analysis tools
- Detects SunBelt sandbox-related virtualized environments.
- Uses anti-debugging methods.
- Detects SunBelt sandbox-related virtualized environments.
- THEFT TARGETS - Steals and leaks sensitive information by accessing:
- Firefox stored credentials databases.
- Internet Explorer stored credentials databases.
- Common software account information
- Outlook account information.
- Outlook preferences.
- Firefox stored credentials databases.
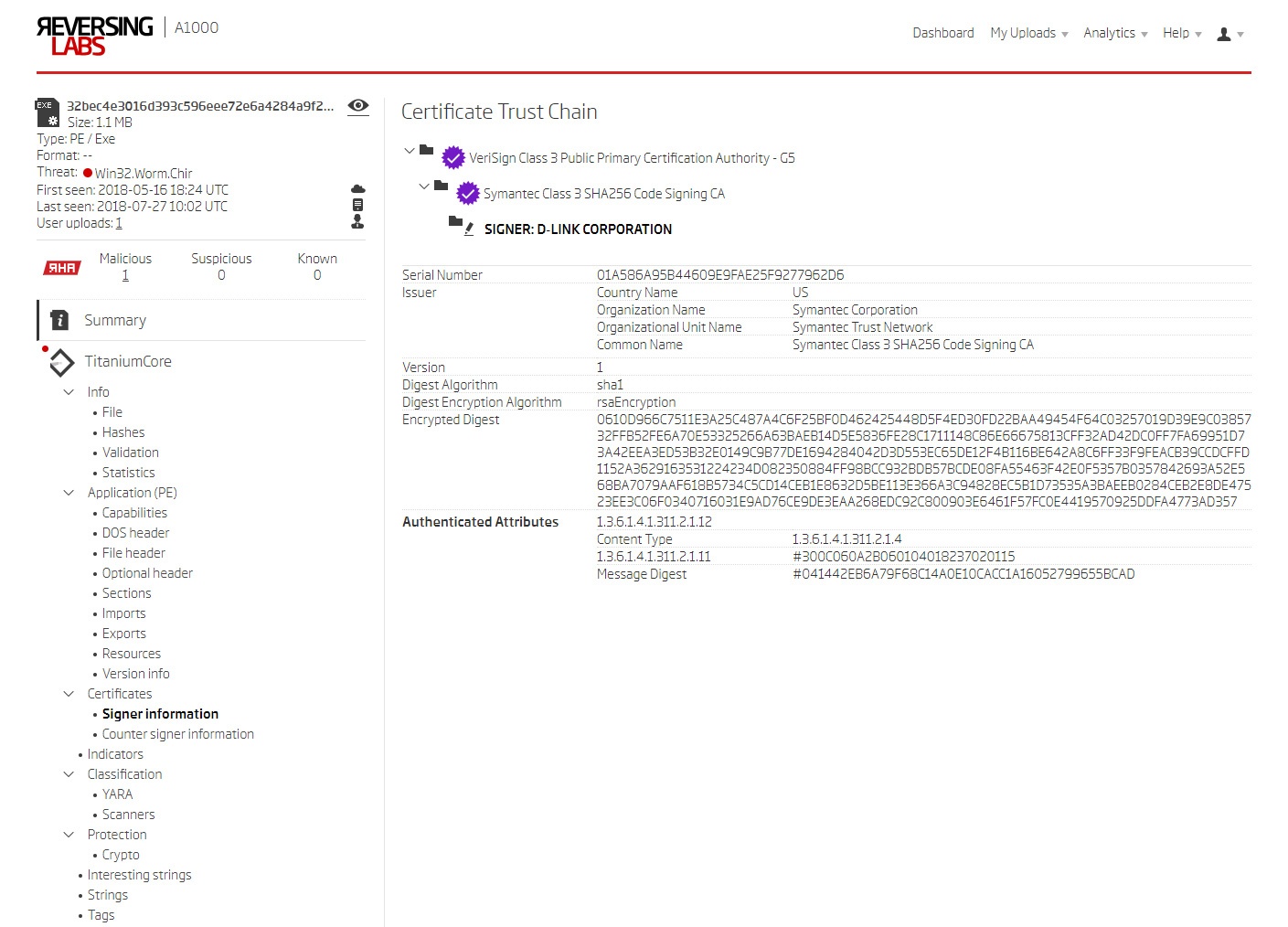
B.) Sample 32bec4e3016d393c596eee72e6a4284a9f2e49ab:
The second sample is a file seemingly signed with a D-Link certificate (cert-serial:01A586A95B44609E9FAE25F9277962D6). In this case, AV engines deliver a verdict of "virus" (NOT "trojan").
One notable aspect of this example was ReversingLabs’ ability to detect an existing D-Link certificate. Other tools and metadata providers (such as Signtool, Sigcheck and VirusTotal) showed no existing certificates. Those tools miss because virus injection disrupts the certificate chain. The advanced static analysis engine in the ReversingLabs A1000 platform was able to detect a “cert-malformed” and assign a tag to the sample. The certificate information is searchable and enables detection of virus-infected, legitimately signed files.
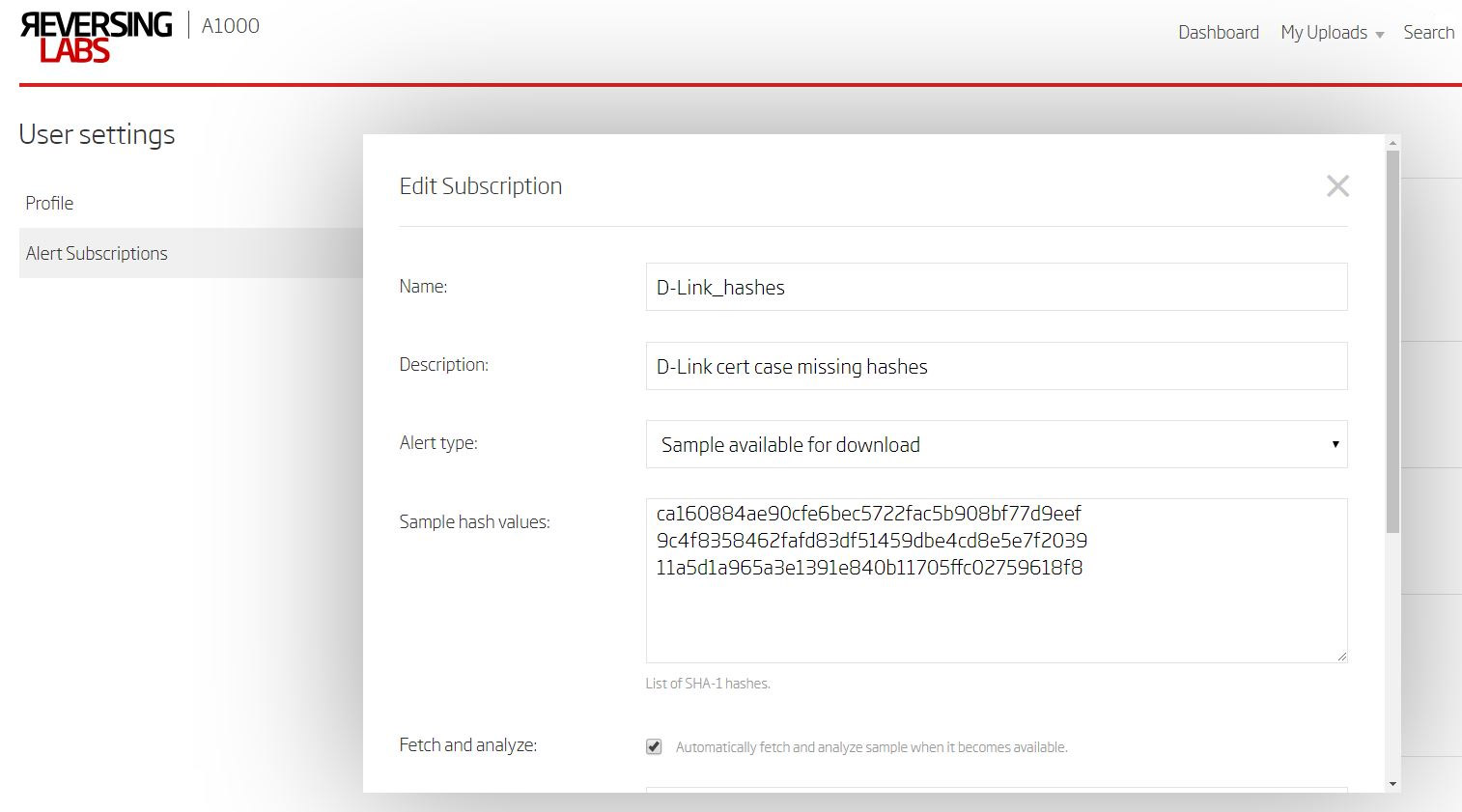
Step 2. - Alerting on missing hashes
ESET published this post at https://www.welivesecurity.com/2018/07/09/certificates-stolen-taiwanese-tech-companies-plead-malware-campaign/
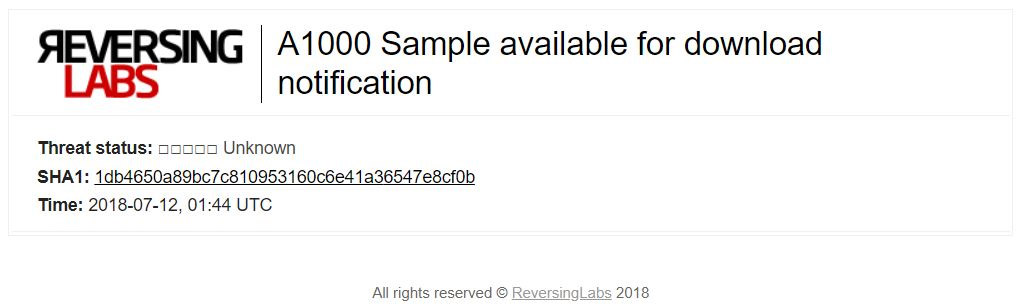
In this post, the hashes for malware using D-Link's stolen certificates were made available to the public. Although the hashes are public, the samples themselves are not (at the time of this writing). RL Research recommends that security teams set notifications when target samples become available for download. ReversingLabs customers can reach out to their support managers to learn how to set up tracking and alerting on target hashes in the product.
Example: Slack Alert on newly available hash
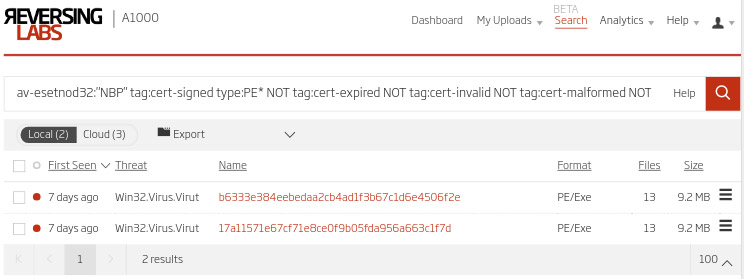
Step 3. - Hunt for certificate misuse
With literally thousands of malicious files taking advantage of valid certificates, there are countless hunting scenarios. For example, hunters can start with an initial search by malware family name, and a specific condition - that executables must be signed with a valid (unexpired) certificate.
Using detailed sample information (above) and drilling down on one of the results shows that malware authors used a valid certificate belonging to Shenzhen Chuang Hui Network Technology Co.
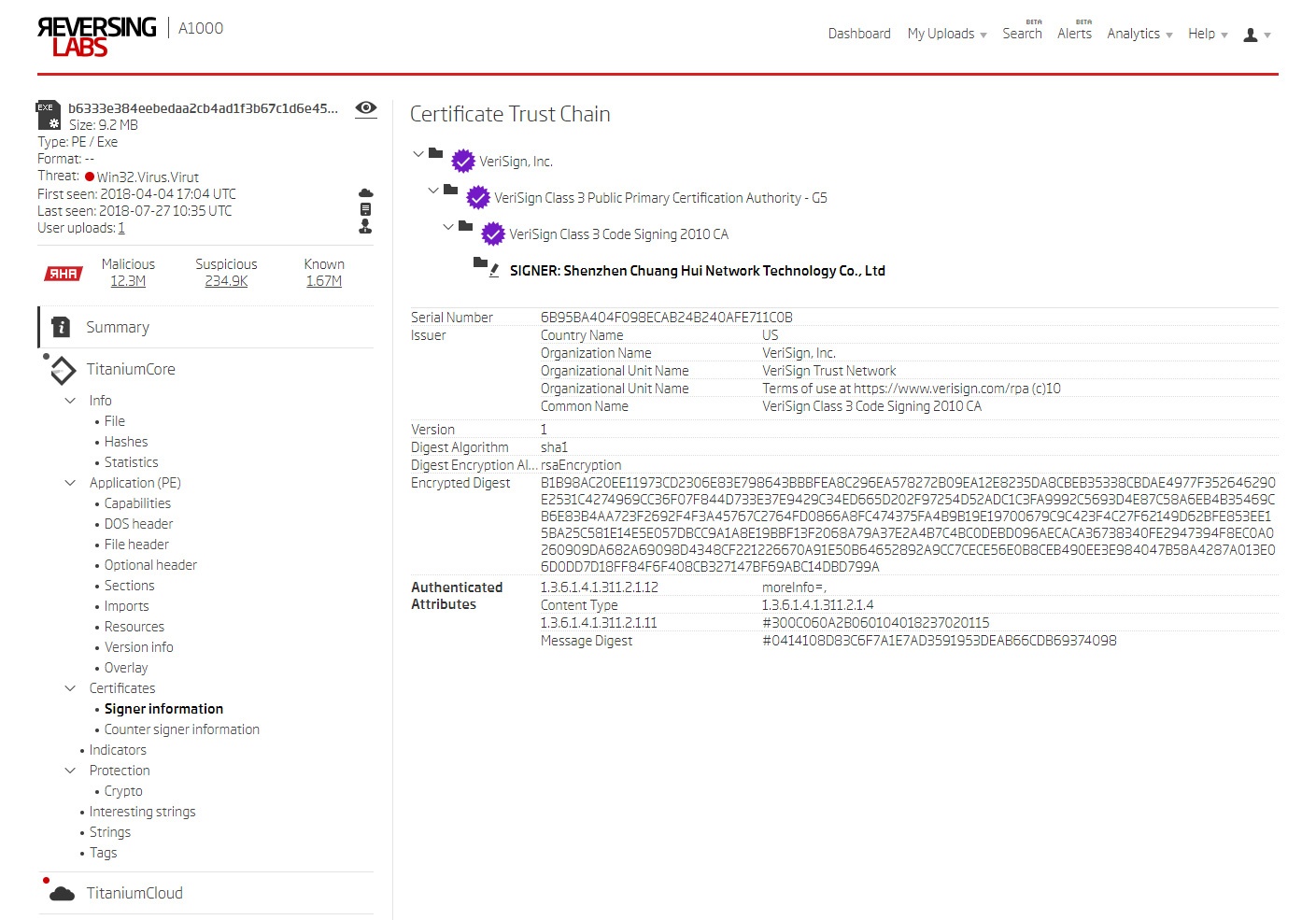
Hunters can then search through the history of all files that have been signed with that specific certificate (code signing certificate cert-serial: 6B95BA404F098ECAB24B240AFE711C0B). Doing so readily reveals the timeline of when the compromise occurred and provides a fast way to double-check if there are any false negatives that should be examined.
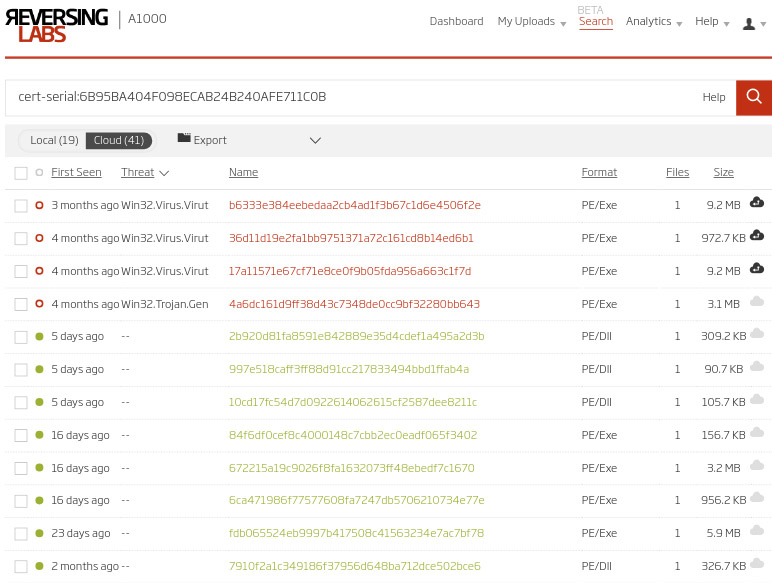
Step 4 - Alerting on certificate misuse
ReversingLabs’ customers typically set automatic alerting on certificate misuse. Other advanced automated reverse engineering/static analysis technologies also support alerting when certificate misuse is detected. The RL Research team strongly recommends that companies take advantage of these alerting capabilities. As the RL Research team uncovers new intelligence or develops new processes, we will share them.
If you’d like to learn more about the malware analysis and hunting the RL Research team uses in our work, a good place to start is checking the ReversingLabs A1000.
Watch for more threat intelligence and hunting blogs from us in the near future, and if you’re planning on attending Black Hat show, please stop by. We’ll be in Booth #1613.
RL Research
Get up to speed on key trends and learn expert insights with The State of Software Supply Chain Security 2024. Plus: Explore RL Spectra Assure for software supply chain security.






