 A survey of more than 300 technology professionals found widespread concern about supply chain attacks, but only sporadic efforts to detect such attacks.
A survey of more than 300 technology professionals found widespread concern about supply chain attacks, but only sporadic efforts to detect such attacks.
In the wake of attacks like SolarWinds SolarStorm and CodeCov, software supply chain security and tampering (unauthorized malicious software modifications) have risen to the top of security teams’ priority list. With software development teams under pressure to deliver their applications faster than ever before, software teams are leveraging open source and third-party software to deliver applications and services at scale. At the same time, application security has shifted left and become an essential practice for software engineers.
This lengthening of software supply chains has dramatically increased the attack surface that skilled cybercriminals can take advantage of. Software publishers today are concerned not only about delivering features on time, but also that their software might make headlines in the next SolarWinds-style attack.
The question is ‘how aware of supply chain threats are software companies,’ and also ‘what are they capable of doing to stop such attacks?’ To try to answer those questions, ReversingLabs commissioned Dimensional Research to conduct a survey of more than 300 professionals at software publishing companies. The survey revealed deep concerns about the threat of software tampering and attacks on software supply chains. It also highlighted the obstacles and challenges that software firms face as they attempt to detect and block attacks on their software development process.
Here are key takeaways from the survey—as well as key data points that your software security team can take action on to protect your organization from such threats.
[ Download the report: Flying Blind: Firms Struggle to Detect Software Supply Chain Attacks ]
Dev team: We have a problem
Attacks like SolarWinds and CodeCov put software supply chain attacks on the radar of development organizations, our survey reveals. How much so? Fully 98% of those surveyed reported that they believe the use of open source code, 3rd party software, as well as the threat of software tampering are directly increasing their security risk today. A large majority - 87% - recognize that software tampering can result in a security breach at their organization.

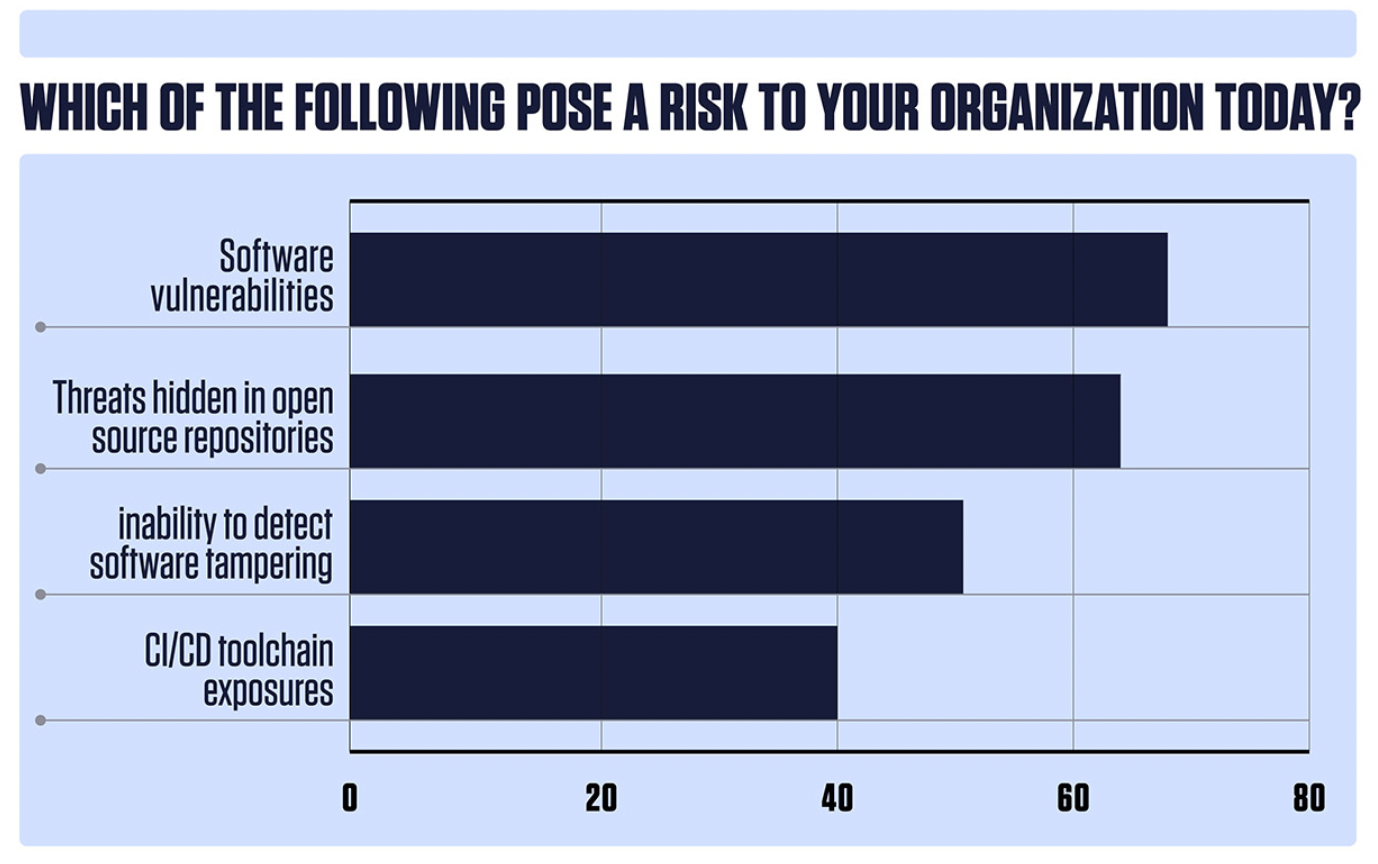
And, in a measure of the increasing prominence that supply chain threats now have, the threats posed by open source repositories ranked second only to software vulnerabilities in operating systems and applications when survey respondents were asked what posed the biggest cybersecurity risk to their organization, with 63% of survey takers saying open source posed a risk to their organization. Other supply chain risks such as the inability to detect software tampering also ranked highly with a majority of respondents (51%) saying it posed a risk to their organization.
Teams not prepared to stop software tampering
While software professionals across the board understand that the risks posed to their organizations are severe, they are not well poised to defend against such threats, our survey revealed. For example, only 51% of respondents reported their companies can protect their software from 3rd party risk when using open source, commercial solutions, and partner software. That’s a worrying statistic in a threat environment in which cybercriminals are increasingly taking advantage of software dependencies. It is even more concerning when one considers that the reliance on third-party and open source software will only continue to grow.
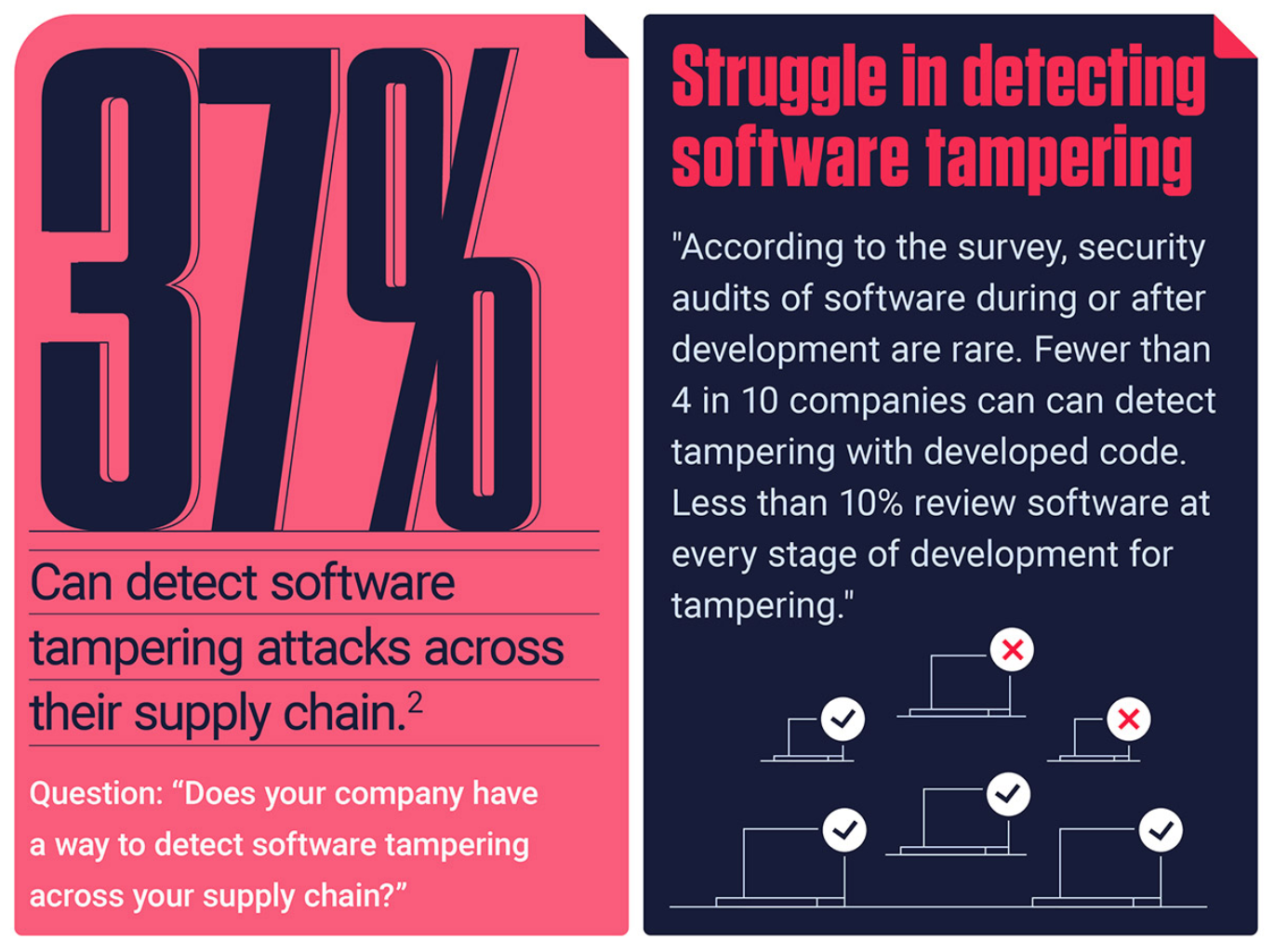
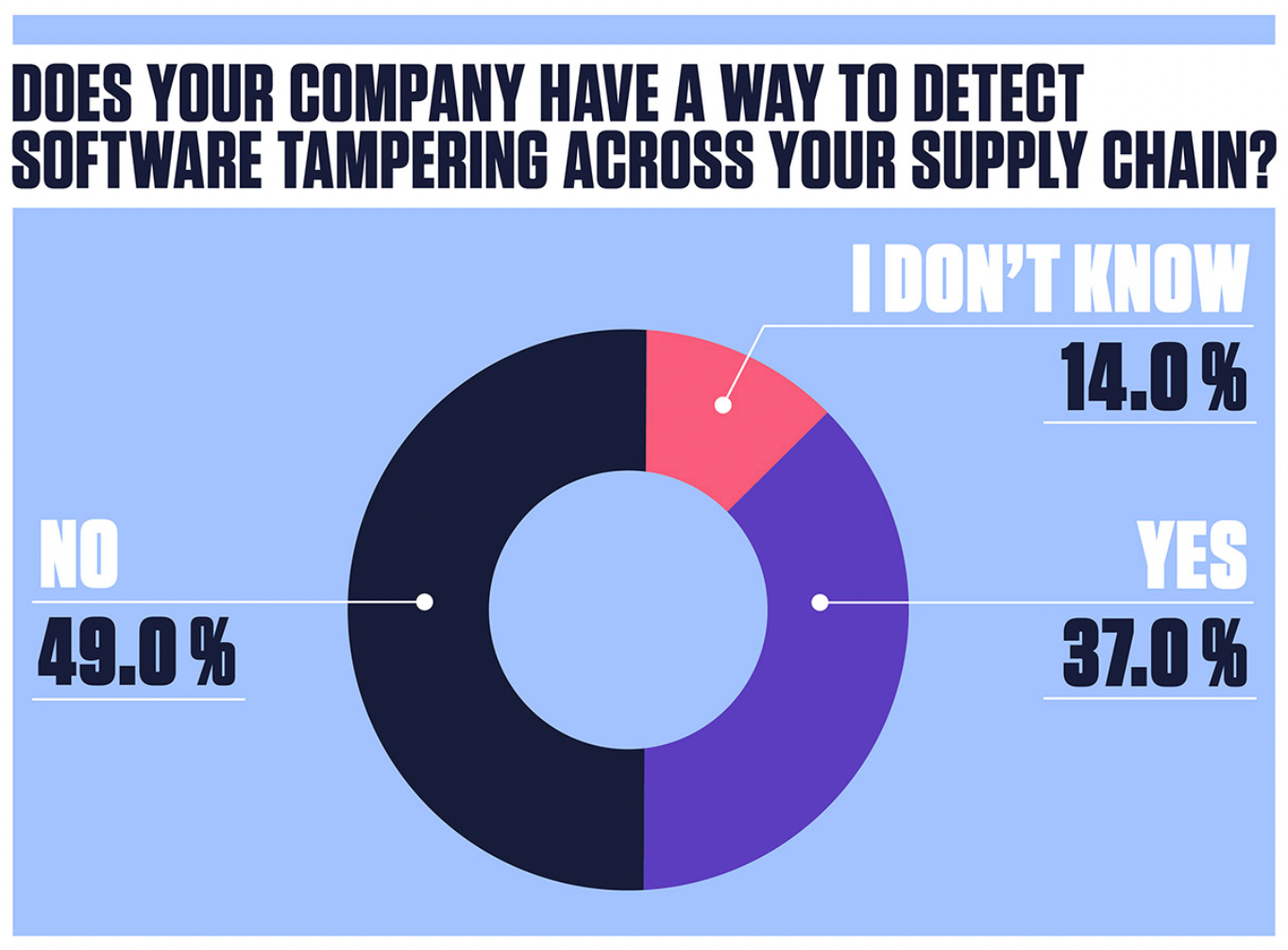
Among these software professionals, just 37% of software companies indicate they have a way to detect software tampering across their supply chain. Even more concerning: of those that claim to be able to detect tampering, a shockingly low 7% do it at each phase of the software development lifecycle, and just one in three actually check for tampering once an application is final and deployed. The inability to holistically detect tampering, coupled with the prevalent release of software with vulnerabilities, creates a growing new attack vector.
Code security still a low priority in software development organizations
Overhanging the issue of software supply chain risk is the even larger and more amorphous issue of software security itself. Behind every vulnerable application, third party plugin or open source module is insecure code. And that insecure code is often the product of development organizations at which secure development processes have yet to take hold, or at which code security is a secondary (or tertiary) priority.
That unfortunate reality was laid bare by our survey respondents, 54% of whom acknowledged that their organization releases software with potential security risks. Software vulnerabilities in published code were the rule rather than the exception: 37% of respondents said their companies release software that is subsequently found to contain security vulnerabilities monthly or more frequently. An even higher percentage (63%) admitted that was the case for software their organization releases at least on a quarterly basis.
Software development organizations need help
It is clear that software companies recognize the risk that attacks on development pipelines and software supply chains pose. But it is equally clear that they lack the bandwidth to meet the security demands of modern DevOps environments.
For example, Software Bills of Materials (SBOMs) have been promoted as a way to track software dependencies and to keep track of the various components within a software package. However, only 27% of software companies generate and review an SBOM today. The reason? 9 in 10 professionals indicated that the difficulty to create and review SBOMs is increasing. When asked why these companies do not generate and review SBOMs, top reasons cited were a lack of expertise (44%) and not being adequately staffed to review and analyze SBOMs (44%). Software companies across the board don’t have the bandwidth internally to properly use this now essential tool.
It’s time to take action
The threat to the software industry is clear, and it’s time for companies to understand the steps they will need to take in order to shore up their defenses. Software companies will have to do a better job of balancing their business goals with security protocols. They’ll also need to turn their awareness of this problem, and their inability to defend against it, into a working plan that utilizes modern and reliable solutions. The threat that cybercriminals pose will only continue to worsen, so the time to act for the software industry is now.
Get the full report: Flying Blind - Firms Struggle to Detect Software Supply Chain Attacks
Get up to speed on key trends and learn expert insights with The State of Software Supply Chain Security 2024. Plus: Explore RL Spectra Assure for software supply chain security.
Keep learning
- Join NIST and other experts: Breaking Down CSF 2.0
- Join the Webinar: Unraveling XZ: A Software Supply Chain Under Siege
- See Special Report: The State of Supply Chain Security 2024
- See Gartner's guidance on managing software supply chain risk
- Learn why/see buyer's guide: Upgrade your AppSec tools for the SSCS era







